
TryHackMe: Advent of Cyber 2023 (Day 5 - 8)
Get started with Cyber Security in 24 Days - Learn the basics by doing a new, beginner-friendly security challenge every day leading up to Christmas.

Get started with Cyber Security in 24 Days - Learn the basics by doing a new, beginner-friendly security challenge every day leading up to Christmas.

Get started with Cyber Security in 24 Days - Learn the basics by doing a new, beginner-friendly security challenge every day leading up to Christmas.
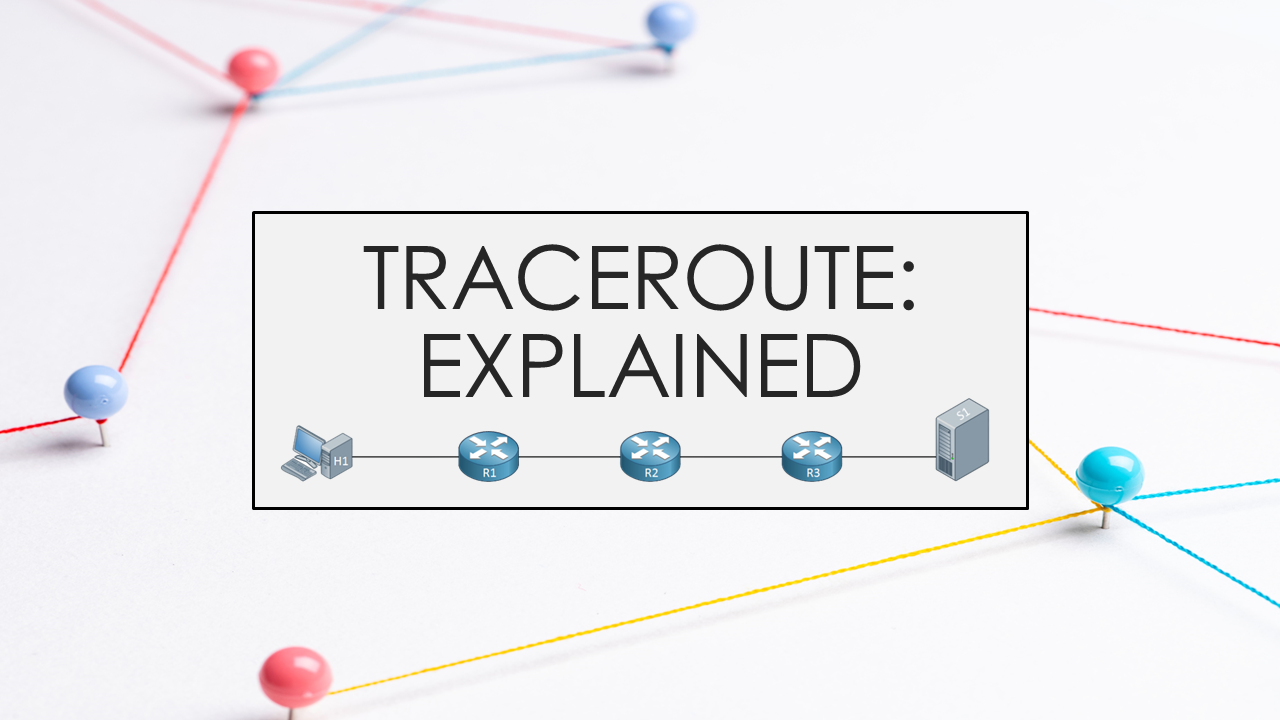
The what, why and how of the network debugging tool traceroute
Create executables from Python code easily using a simple and intuitive GUI

Apply learned skills to probe malicious emails and URLs, exposing a vast phishing campaign

You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth

Learn the basic tools and techniques used in vulnerability assessment and exploitation in a gamified manner

Learn the basic tools and techniques used in vulnerability assessment and exploitation in a gamified manner

Learn the basic tools and techniques used in vulnerability assessment and exploitation in a gamified manner
DHCP the protocol that enables automatic assignment of IP addresses to hosts on a network
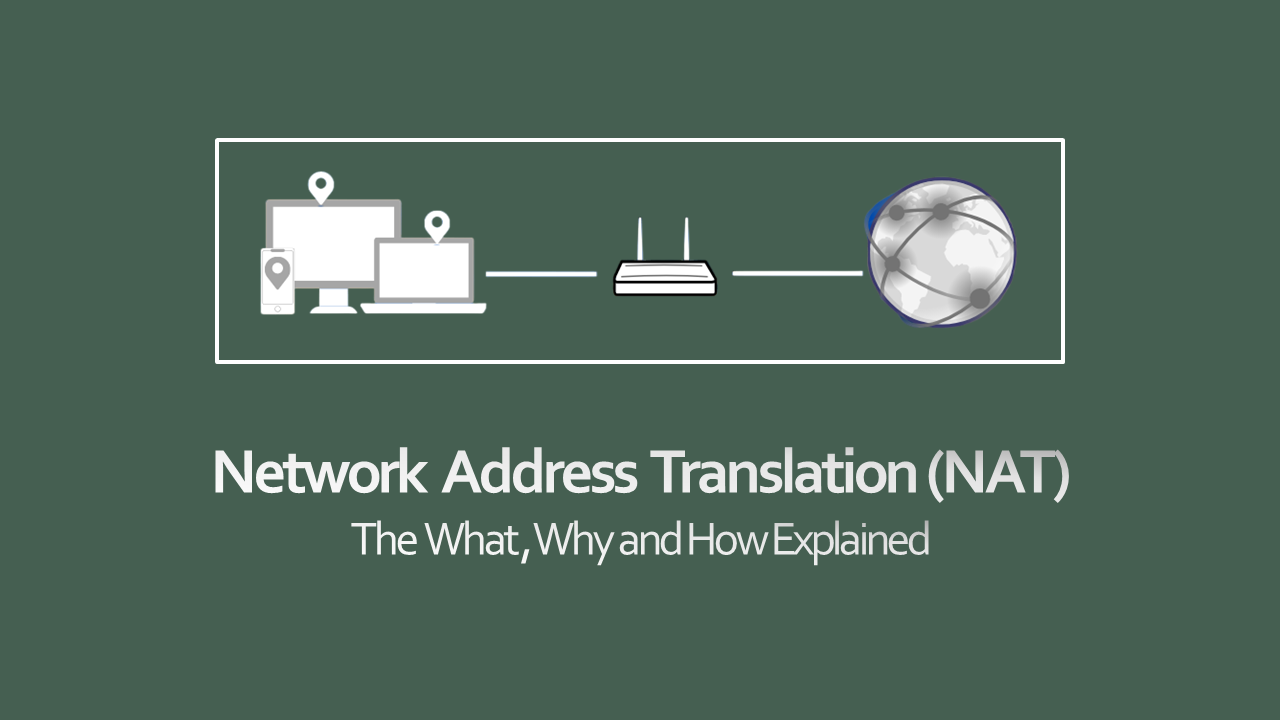
Overview of NAT the private IP to public IP translator

Exploring DNS the phonebook of the internet

Regex (also called Regular Expression or RegExp) is a sequence of characters that can be used to find or match patterns in text. Regexes are made up of special characters that enable us to define c...

An introduction to the directories that makeup the Linux Filesystem

Docker containers are used to run applications and services in an isolated environment. Any data that is generated by the container is only stored while the container is running i.e. data generated...